On June 13th, 2025, Israel launched Operation Rising Lion, a coordinated military campaign targeting key Iranian nuclear and military assets. The operation marked a pivotal moment in the ongoing hostilities between the two countries, as it not only escalated the physical conflict between them, but also sparked a parallel surge in cyber activity. Between June 13th and June 17th, 2025, multiple cyberattacks by 74 hacktivist groups were observed, with 67 considered pro-Iranian and identified launching attacks against Israeli military targets. As is typical of hacktivist attacks, the majority of these incidents involved distributed denial-of-service (DDoS) attacks, website defacements, and data leaks. However, many of the claims surrounding these attacks appear to be exaggerated or unverified, a common trait in influence-driven cyber operations designed as much for psychological effect as for physical disruption.
This blog will explore these attacks in greater detail, examining the actors involved, the tactics employed, and the broader strategic and symbolic impact of cyber activity during this conflict.
Iranian Cyber Operations
In the aftermath of Operation Rising Lion, Iranian-linked cyber actors intensified their digital offensives against Israel. These operations encompassed a wide variety of activities, from disruptive attacks on critical infrastructure to psychological warfare aimed at undermining public morale.
Targeted Entities and Tactics
Iranian cyber campaigns have predominantly targeted Israeli government, defense, telecommunications, finance, media, education, and emergency services sectors, with the tactics employed ranging from DDoS attacks and website defacements to data breaches and unauthorized system access, but also disinformation. For example, Group-IB researchers identified instances where Iranian-affiliated threat actors manipulated Israeli emergency alert systems, disseminating false warnings about ammonia leaks and terror attacks to incite panic and lure civilians from shelters.
GPS spoofing incidents have also been reported, affecting maritime and aviation navigation systems in Israel and neighboring countries such as Egypt, Jordan, the UAE, Pakistan, and Saudi Arabia. Iranian actors have also targeted civilian surveillance infrastructure, with former deputy director general of Israel’s National Cyber Directorate, Refael Franco, warning citizens to secure or disable home security cameras, citing Iranian efforts to access these systems to assess missile impact sites and improve precision.
This wide spectrum of attack techniques demonstrates the increasingly hybrid nature of Iranian cyber strategy. The convergence of psychological operations, intelligence gathering, and disruptive attacks indicates a shift towards campaigns designed to destabilize the Israeli state and its populations simultaneously.
Hacktivist Operations
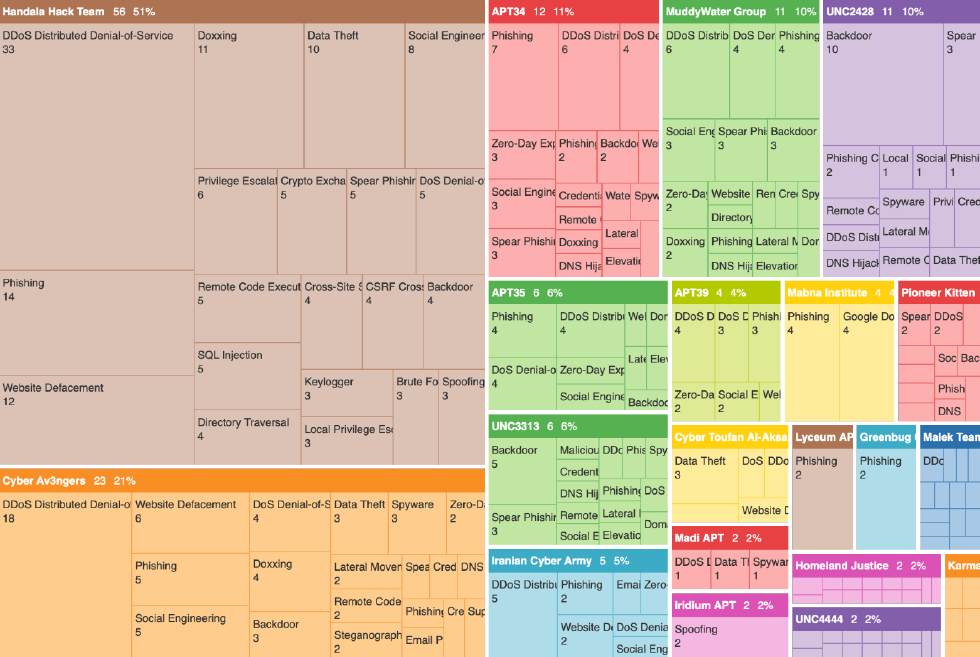
Pro-Iranian hacktivist groups have played a significant role in influencing the ongoing conflict between Israel and Iran, with the self-proclaimed pro-Palestine hacker group Handala particularly active and having claimed responsibility for multiple high-profile attacks. On June 23rd, 2025, Handala claimed to have obtained and published the coordinates of Israeli shelters allegedly housing high-profile individuals, accompanied by a warning urging civilians to evacuate. In addition to this psychological operation, the group expanded its targeting to include Israeli employment and staffing companies, such as JobPlace Ltd and QHR Ltd, claiming to have exfiltrated large volumes of sensitive data. Other hacktivist groups, such as Mr. Hamza, TEAM FEARLESS, and Arabian Ghosts, have also been active, conducting DDoS attacks, website defacements, and data breaches targeting Israeli government and public sector entities.
Hacktivist groups have also used their Telegram channels to amplify their attacks and geopolitical narratives, which includes reposting claims of attacks by affiliated or ideologically-aligned collectives. This content typically includes pro-Iranian and pro-Palestinian narratives, with one notable trend involving the use of video footage depicting missile strikes and drone operations, alongside images of Iranian casualties.
Iranian APT Activity
In addition to widespread hacktivist campaigns, Iran-linked advanced persistent threat (APT) groups have also been active throughout the conflict. A recent campaign, observed by Check Point researchers and attributed to the threat actor Educated Manticore, has been targeting Israeli academics and cybersecurity experts with spear phishing emails since mid-June 2025, directly coinciding with physical attack campaigns. The phishing efforts aim to direct victims to fake Gmail, Outlook, or Yahoo login page, or Google Meet invitations to steal credentials. One message also suggested an in-person meeting, indicating that the campaign may extend beyond cyberspace. APT groups such as APT42, APT34, and MuddyWater have historically targeted Israeli government agencies and critical infrastructure, employing targeted phishing campaigns and supply chain attacks to infiltrate and compromise targets, commonly focusing on intelligence gathering and maintaining persistent access to critical systems. These operations are typically long-term and reflect strategic espionage goals rather than immediate, disruptive effects. Many of these operations are also believed to be executed through a network of contractors and front companies, enabling operational flexibility while allowing the Iranian state to maintain plausible deniability. This outsourcing model not only expands operational capacity but also complicates attribution, blurring the lines between state-sponsored activity and proxy operations carrying out attacks on behalf of the Iranian government.
Israeli Cyber Operations
Compared to the broader range of Iranian-linked cyber activity, Israel’s cyber operations have been comparatively limited, though information about clandestine cyber operations being conducted simultaneously with the physical attacks may yet still emerge.
The main group observed carrying out attacks is Predatory Sparrow, a hacktivist group widely believed to be linked to the Israeli government. The group notably targeted Bank Sepah on June 17th, 2025, and the Iran-based cryptocurrency exchange, Nobitex, only a day later.
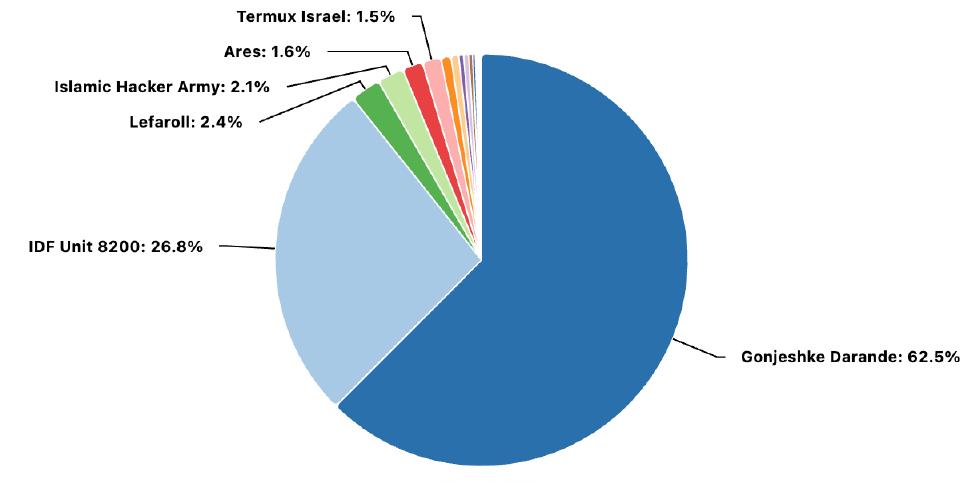
The attack on Bank Sepah disrupted customer services, affecting access to accounts, withdrawals, and card payments, and even forcing several branches to close temporarily. Users also reported service failures with cards issued by Kosar Bank and Ansar Bank, with both financial institutions linked to Iran’s military. The incident may have also impacted gas stations across the country. Predatory Sparrow stated that the operation was retaliation for Bank Sepah’s alleged involvement in financing Iran’s military and nuclear programs. In the attack on Nobitex, Predatory Sparrow alleged it had stolen over $90 million in cryptocurrency, but the funds were not retained. Instead, they were sent to vanity addresses, effectively destroying them and signalling that the operation was not financially motivated. The group accused Nobitex of playing a central role in financing Iran’s military activities and broader regional influence campaigns.
Cyble researchers also observed the deployment of the IRATA Android malware to target banking applications in Iran. The malware has impersonated legitimate government services, including the Judicial System and the Ministry of Economic Affairs and Finance, and targets more than 50 banking and cryptocurrency applications.
In response, Iran reportedly slowed down internet access to prevent Israel from targeting the country with further cyberattacks, with NetBlocks observing a significant reduction in internet traffic in Iran. Reports have also emerged of the Iranian government urging citizens to delete WhatsApp due to it allegedly having been weaponized by Israel to spy on users. WhatsApp has denied the allegations.
Despite an initial spike in hacktivist activity following Operation Rising Lion, by June 20th, 2025, a drop of 70% was observed in the Middle East after. The decline represents a growing trend in recent hacktivist activity, with these groups now shifting towards short, reactive bursts tied to geopolitical events rather than sustained campaigns. Nevertheless, with continued heightened tensions in the Middle East, threat actors are likely to continue to target the region, motivated by the current geopolitical climate, with Iran in particular considered to be more likely than ever to retaliate through cyberattacks.
Cybersecurity Implications Beyond the Middle East
While the majority of cyber activity during the Israel-Iran conflict has centered on the region itself, there are growing signs that cyber threats related to the Israel-Iran conflict are extending beyond the two countries. In response to the evolving geopolitical climate, multiple United States federal agencies have issued joint advisories warning that Iranian threat actors may attempt to exploit vulnerable networks in the US. Of particular concern are defense industrial base companies, especially those maintaining partnerships or ties with Israeli defense and research organizations, which are considered to be at increased risk. In a related advisory, the US Department of Homeland Security warned of an increase in low-level cyberattacks against US networks by pro-Iranian hacktivists and threat actors affiliated with the Iranian government. These efforts have largely focused on exploiting poorly secured systems, but concerns have also been raised about the potential for violent extremists mobilizing to violence in response to the ongoing conflict in Iran. The timing of the bulletin, issued shortly after US missile strikes on three Iranian nuclear facilities, suggests a heightened state of alert in anticipation of further retaliatory activity in cyberspace.
Outside of the US, Iranian-affiliated actors have also targeted European networks. On June 20th, 2025, Homeland Justice, a group believed to be linked to Iranian state intelligence, claimed responsibility for a cyberattack on the official website of Tirana, Albania. The group alleged that it had exfiltrated sensitive data and wiped city servers, later sharing screenshots of backend access and source code on Telegram. Homeland Justice cited Albania’s continued hosting of over 3,000 members of the Iranian opposition group Mujahedin-e Khalq as the motivation behind the attack.
These incidents demonstrate how cyber conflict related to Israel and Iran’s confrontation is spilling over onto the global stage. As political tensions rise, so too does the risk to international organizations, government systems, and critical infrastructure, particularly those perceived to be aligned with either side of the conflict.
If you would like to know more about how intelligence from Silobreaker can help you keep up to date with ongoing geopolitical issues and understand how they feed into the cyber threat landscape, download our latest report Global Conflicts in the Digital Age – How Geopolitics Influence Cyber Operations

