The discipline of cyber threat intelligence (CTI) has matured considerably in the last year, with organizations from a variety of industries adopting it to support their overall security operations, according to the newly released SANS 2023 CTI Survey. Geopolitical events, particularly the Russia-Ukraine war, have played a pivotal role in convincing organizations that CTI should be considered a central operational requirement.
The survey, co-sponsored by Silobreaker, assesses the responses of 984 individuals working in relevant cybersecurity roles, and representing 25 different industries, including financial services, banking and insurance, government and tech.
While there is clear evidence that CTI is gaining traction amongst these organizations, the report also highlights some areas for improvement. This blog breaks down the key findings of the new SANS 2023 CTI Survey, showing where CTI stands today, and discussing what can be done to better-help CTI teams in their important work.
CTI is gaining in prominence
Encouragingly, the survey findings show promising growth in the number of businesses and government organizations thinking strategically about their CTI requirements, with 59 percent of respondents stating they have clearly defined their threat intel needs, up from 35 percent in 2022.
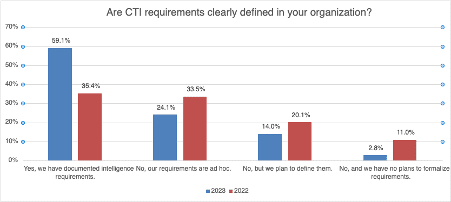
This focus is necessary; if an organization doesn’t think hard about its CTI needs, it could end up gathering and analyzing intelligence which doesn’t reflect the actual risks it is facing. Defining CTI requirements is integral to the planning and direction phase of the intelligence cycle. A lack of focus here could leave organizations rudderless and unable to respond to evolving and potential threats.
Just as reassuringly, the number of respondents with no CTI requirements and/or no plans to introduce them dropped from 11 percent in 2022 to just three percent in 2023.
Half of respondents are measuring the effectiveness of their CTI program, and 87 percent report that CTI has helped to improve security prevention, detection and response.
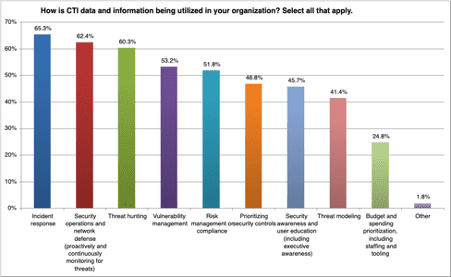
Among CTI teams that track the effectiveness of their programs, the most common methods of measurement are first automated, and then manual, tracking of the actions being taken based off of CTI. Many also calculate the time it takes to respond to an alert or incident as a measure of impact. This suggests that while CTI might not prevent all incidents outright, it can play a key role in reducing response times to an issue.
External news and open sources drive decision making
The survey also reveals the variety of sources CTI teams use to conduct their analyzes, shining a light on which datasets have most influence over organizational decision making. External sources such as news and media reports are most popular, used by 69 percent of CTI teams in their work. Open-source feeds are a close second (at 60 percent), while approximately half (51 percent) of respondents consider internal sources, such as incident response and forensics data.
When it comes to how CTI teams spend their time, over 60% of respondents spend more than half their time responding to open-sourced reporting from others. This includes sources like research reports and cybersecurity news.
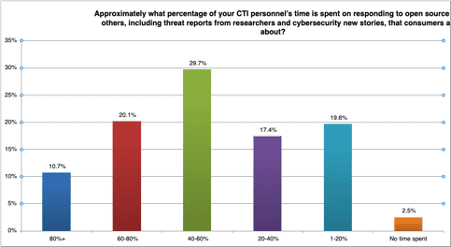
This emphasis on open-source reporting – and the subsequent need to address the numerous questions it raises – indicates that the field of CTI could benefit from additional best practices and processes, especially when it comes to the risks associated with disinformation.
The choices CTI teams make regarding sources matter. The quality of intelligence can vary greatly between sources, while an over reliance on a few sources can lead to blind spots. For example, internal sources containing intrusion data are likely to provide very specific insights about the threat actors targeting an organization. This information is unlikely to appear in news reports or social media forums.
These new survey findings suggest that CTI teams could benefit from expanding their horizons, being more open to the types of sources they consider when making judgements.
CTI tools and resources
Although there is more strategic focus on CTI, respondents did indicate that there are a number of obstacles that prevent them from carrying out their work thoroughly. Almost half (44 percent) said skills and training were lacking, and when asked about budgets, 39 percent said their CTI programs had insufficient funding. This feedback suggests CTI teams could do more to secure buy-in from senior management and convince them of the value of their work.
Additionally, 42 percent of respondents report that a lack of automated tools is holding them back. In terms of tools, 59 percent use security information and event management (SIEM) solutions or other security analytics platforms, and 48 percent of CTI teams use a threat intelligence platform (TIP).
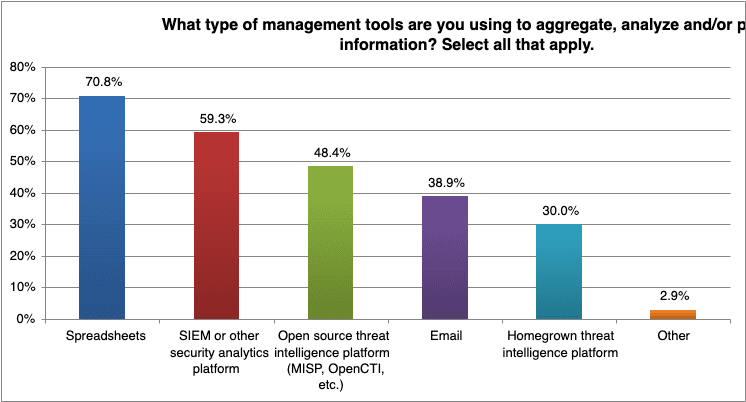
As seen in previous years, spreadsheets remain the most popular tool for CTI teams, with 71 percent using them to arrange information, in spite of the availability of CTI-specific tools.
Geopolitical unrest drives CTI adoption
Russia’s invasion of Ukraine in February 2022 sent ripples through the world and there’s little doubt this caused organizations to reassess their CTI strategies. Indeed, 71 percent of respondents stated that geopolitical developments now play a very or somewhat important role in determining their intelligence requirements.
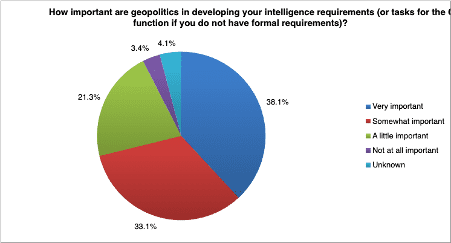
This is an understandable response; conflict in the battlefield is increasingly spilling over into cyberwarfare, with Russian state-sponsored attacks proliferating and becoming more sophisticated. This blurring of the lines between physical and cyber threats underlines the need for CTI teams to consider as broad a range of intelligence sources as possible. It’s only by layering physical, cyber and geopolitical intelligence on top of each other that organizations can accurately assess all the risks posed by such fast-moving events.
How Silobreaker supports CTI requirements
Silobreaker can support CTI teams at all stages of the intelligence cycle, giving them access to a single, automated, source-agnostic platform that allows for them to manage cyber, physical and geopolitical priority intelligence requirements (PIRs) in one place. By automatically collecting and processing structured and unstructured data from open sources – as well as from the deep and dark web and via finished intelligence sources – Silobreaker
gives organizations, even those with limited resources or small intel teams, the ability to cast their intelligence net as wide as possible, and then collate and analyze all this vital information in one dashboard.
This capability is important when trying to secure management buy-in. With Silobreaker, it’s simple to create and disseminate tailored reports and alerts, which give management teams and other stakeholders full visibility into the risks facing their own operations, speeding up their decision-making processes. In doing so, it also shows the value of the work undertaken by CTI teams. To learn more about what Silobreaker can do to address your CTI needs, check out our Cyber Threat Intelligence page.
Download the SANS 2023 CTI Survey: Keeping up with a changing threat landscape, to read the full insights.

