Just as the Russia-Ukraine war sparked an increase in cyberattacks and disinformation campaigns, so has the recent war between Israel and Hamas. This increase was seen almost immediately following the attack by Hamas on October 7th, 2023, and subsequent response by Israel. This comes as no surprise, as physical confrontations nowadays are increasingly accompanied by parallel online activity. Most of the currently observed activity relates to hacktivism and disinformation campaigns – though some state-sponsored hacking campaigns are also likely being carried out behind the scenes.
The re-emerging trend of hacktivism and disinformation in the Israel-Hamas conflict
Though hacktivist activity surrounding the Israel-Palestine conflict has been ongoing for years, the scale at which this is now observed has grown immensely. Just four days after the initial attack by Hamas, over 100 different hacktivist groups announced their participation in the conflict, with most taking a side. Over 70 groups have proclaimed to be pro-Palestine, while a small number are pro-Israel, or in some cases just anti-war. The groups come from various countries, including Russia, Ukraine, India, Pakistan, Malaysia, Bangladesh, Morocco and Iran. They include well-known groups like Anonymous Sudan, Killnet, ThreatSec and Team Insane Pakistan, as well as newly formed groups, such as Libyan Ghosts, Garuna Ops and SilentOne.
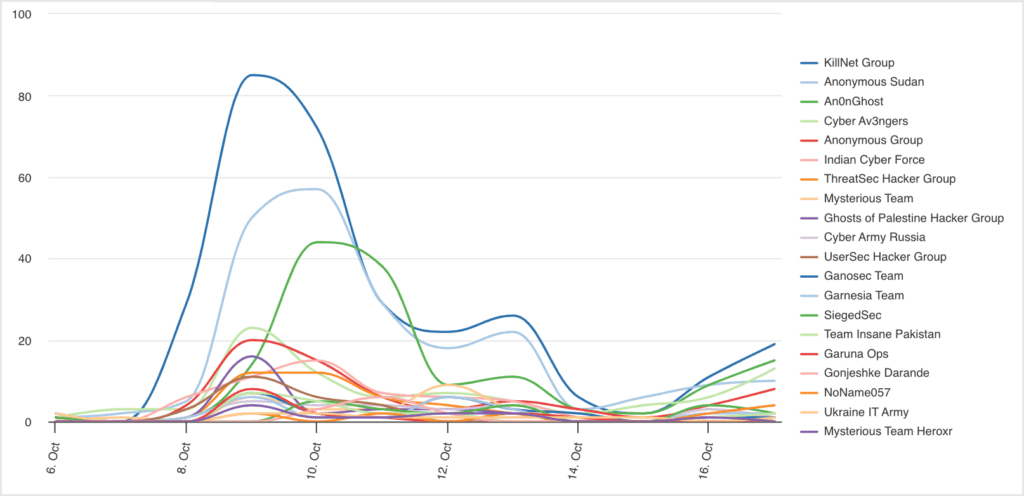
Most attacks are currently distributed denial-of-service attacks and website defacements, which are generally not very long-lasting and quickly remediated. Though these types of attacks might be more of a nuisance than cause any actual damage, they can have serious impacts in real life. Various attacks have targeted government and media sites, which individuals impacted by the war will likely rely on heavily for any news on the current situation. Other targets have included the websites of critical infrastructure organizations, such as the Israel Independent System Operator and the Israel Electric Corporation, both claimed by Cyber Av3ngers.
Some groups have also claimed to have conducted data theft attacks. For example, Team Insane Pakistan claimed to have stolen data from an Israeli hydroelectric power plant. RansomedVC group has reportedly expressed interest in buying access to systems in Iran, Palestine, and Gaza, potentially for the purpose of obtaining system data related to the ongoing conflict.
On the other side of the spectrum are the threat actors that aim to cause more destructive attacks. The global hacktivist collective, AnonGhost, claimed to have targeted RedAlert, the app that provides real-time rocket attack notifications in Israel, to send out fake nuclear attack alerts. Anonymous Sudan, believed to be Russia-aligned rather than Sudan-based, similarly claimed an attack on RedAlert, as well as the Tzeva Adom alert application and Israel’s Iron Dome. This group also claimed multiple attacks on industrial control systems (ICS) in Israel, including the Israeli Global Navigational Satellite Systems, Building Automation and Control Networks and Modbus ICS.
Internet connectivity in the region has also been down sporadically. Netblocks stated that whilst there is some slight connectivity, most of the ISPs based inside of Gaza are gone as of October 10th, 2023. Some of the downtime has been attributed to missile attacks; however, in some cases, hacktivists have also claimed to be responsible for the outages. For example, ThreatSec claimed to have breached the Palestinian internet service provider (ISP), Alfanet. Regardless of whether it is missiles directed at fibre optic cables or hacktivists that take down an internet provider, any downtime in such a vital service can have immense consequences for individuals in the conflict zone. For example, the Israeli government reportedly used Facebook to warn residents of al-Daraj to evacuate their homes in advance of impending airstrikes, with these warnings never reaching the residents because of the outages.
The sheer amount of hacktivist activity related to the ongoing conflict comes as no surprise. A surge in hacktivism was previously seen in relation to the Russia-Ukraine war, with this activity only setting a precedent for future conflicts. Though perhaps not as prominent in the news, the same kind of activity was seen when the Nagorno-Karabakh conflict between Azerbaijan and Armenia re-emerged in October 2023. In fact, it has become so commonplace, that the International Committee of the Red Cross published rules of engagement for civilian hackers involved in armed conflicts, warning that an unprecedented number of people are joining patriotic cyber groups. The humanitarian-based rules include not conducting direct attacks against civilian objects and medical and humanitarian facilities, not using hacking tools that spread uncontrollably and not spreading terror among the civilian population. Whether or not hacktivist groups will adhere to these rules remains to be seen, with some groups already indicating that they will not abide by them.
Possible activity by advanced persistent threat actors
Hacktivists are not the only groups to have entered the digital conflict, with the sophisticated hacking group, Predatory Sparrow, having re-emerged after a period of dormancy following the start of the war. The group has suspected links to the Israeli government and a history of conducting destructive attacks against entities in Iran. The group’s re-emergence was accompanied by a message stating ‘We hope you’re following what is happening in Gaza’.
This suspected nation-state actor is not the only group interacting with the tensions between Israel and Palestine, either during the current conflict or before. Earlier in the year, Microsoft identified a Gaza Strip group, tracked as Storm-1133, targeting energy, defense, and telecommunications companies in Israel. The group used fake LinkedIn profiles impersonating software developers or project managers to install backdoors. Storm-1133 is believed to work to advance the interests of Hamas.
Though there have not been many public reports on state-sponsored activity directly related to the ongoing fighting, such activity is likely to take place in the background. As nation-state activity is much more covert compared to the very vocal activity of hacktivists, any analyzes on such campaigns will take more time, especially with regard to making confident attributions to specific threat actors.
How disinformation is blurring the lines between fact and fiction
The physical and cyber conflict has been accompanied by a rapid and expansive spread of disinformation across social media, including platforms such as Instagram, X (formerly Twitter), TikTok, Facebook and Telegram, emanating from both sides. Fake accounts on X impersonating journalists from the BBC and Jerusalem Post have been used to spread misleading information, including false reports that Prime Minister Benjamin Netanyahu has been taken to hospital. Video game footage shared on X has been promoted as a Hamas fighter shooting down an Israeli helicopter, videos of airstrikes in Syria are being claimed as Israeli strikes in Gaza, and images of fireworks and celebrations by football fans in Algiers claim to be bombings in Gaza. X’s owner Elon Musk has himself been caught promoting two particularly virulent accounts spreading disinformation in a post that was viewed 11 million times before Musk deleted it.
Disinformation has also been spread purposefully by individuals and groups seeking to enhance a certain narrative, notably Russian propaganda on Telegram channels attempting to discredit Ukraine by spreading fake reports that Hamas is using weapons from Ukraine. Known propagandists have reportedly joined this information campaign, with videos released featuring Western weapons with captions that thank Ukraine.
Social media has not been limited to the spread of disinformation, but has also been used to spread fear, terrorise and broadcast acts of war. In one instance, a girl found out that her grandmother had been killed by a militant after the man broadcast it on a Facebook livestream from the woman’s own account. The fear of further violent and disturbing content being spread on social media has resulted in numerous warnings to parents to delete social media applications from their children’s phones.
As the overwhelming amount of content surrounding the conflict appears online, separating the legitimate stories from disinformation becomes increasingly difficult, particularly with the growing trend of using video games and recycled news footage. The social media platforms facilitating this disinformation are being called out and criticised for letting it happen. A caution from the European Commissioner was issued to X, who accused the platform of spreading ‘illegal content and disinformation’ in violation of the European Union’s Digital Services Act. Following the caution, the European Commission sent a formal request for information, with certain US political leaders also calling on the platforms to better enforce their terms of services.
X has furthered the spread of disinformation through its decision to sell account verification, making it easier for such information to be spread by ‘blue tick’ accounts. The platform’s trust and safety team, which was charged with overseeing global content moderation, has also reportedly been radically diminished. The company has removed some fake tweets, but often not until hours after they were posted, with many of the purveyors of the information still operating freely on the platform. X has since claimed it will remove any Hamas-affiliated accounts and is reportedly coordinating with industry peers to try and prevent the distribution of terrorist content.
Closing thoughts
The activities above demonstrate just how quickly physical conflicts are mirrored in the cyber world, and vice versa. Hacktivists have always been very active in using cyberattacks to further the real-life causes that they strive for. Just as the war in Ukraine resulted in many threat actors taking sides, so has the ongoing Israel-Hamas war, with such activity expected to continue if the conflict ensues. Additionally, it is not only hacktivists that one needs to be aware of, but also the more subtle cyberattacks carried out by nation-state actors or more generally advanced actors. Combine all this with disinformation spread across various channels and it can easily lead to confusion over the true state of the situation, possibly impacting the decision-making of individuals in leadership positions.
If you would like to know more about how Silobreaker can help you keep up to date with ongoing geopolitical issues and understand how they feed into the cyber threat landscape, contact us here.

