What is the core of the intelligence cycle?
The intelligence cycle is a step-by-step process for gathering, analyzing and synthesising data to produce and share useful intelligence. The intelligence production cycle is commonly associated with military and law enforcement agencies, but its principles and methodologies are also used in other sectors. Law enforcement, in particular, uses it to collect relevant information, investigate cases, prevent crimes, stop threats, and keep the public safe. The intelligence cycle consists of several interconnected stages that ensure a structured and organized approach to intelligence operations.
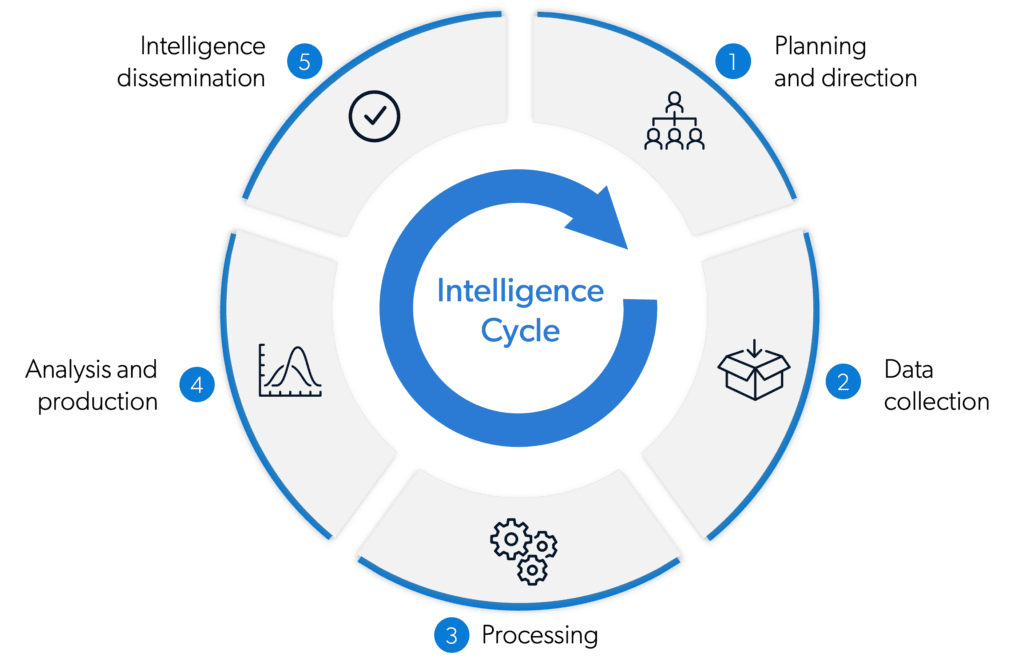
How many steps are there in the intelligence cycle?
The key stages of the intelligence cycle typically include:
1. Planning and direction
The first step of the intelligence cycle requires setting priorities based on the goals of the end user of the intelligence. This can range from parties at various levels of government – national, regional and local – to policymakers, executives, investigators and law enforcement – all with different information needs. For law enforcement like the FBI, this can mean choosing which areas to focus on – such as organized crime, counterterrorism or cyber threats – and then developing strategies to address those areas. Planning and direction guide all 5 phases of the intelligence cycle.
2. Collection
Collection is the second step and it involves gathering and reporting the data needed to produce the finished intelligence. This information can be gathered from a number of sources, such as open sources like public records, media reports and the Internet. Military and law enforcement may consult confidential sources, through interviews, undercover work and surveillance.
Depending on the end user’s intelligence objectives, there may be a specific type or types of collection required. This impacts how much and what kind of data needs to be collected.
3. Processing
After data is collected, it needs to be processed into a usable format. This can require sorting and indexing of data into files, as well as language translation, decryption and interpretation. How the data is processed and collated depends on the collection plan, the overall strategy for analysis and the end user’s goals.
4. Analysis and evaluation
In the analysis and evaluation phase, the processed data is examined and analyzed to extract meaningful insights. Analysts assess the reliability, validity, timeliness and relevance of the information. They contextualize the data, produce assessments and offer judgments on its implications for the end user. The results of this analysis range from brief reports to extensive studies, addressing strategic, operational or tactical intelligence needs. This phase can include the monitoring of current events, forecasting criminal activity and warning decision makers about potential threats.
5. Dissemination
The final stage of the intelligence cycle is the distribution of the finished intelligence to its intended recipients – the end users who generated the intelligence requirements. For example, government intelligence services like MI6 or CIA can then use the final product of the intelligence cycle to assess threats against national security or support foreign policy objectives and military operations.
These recipients can then make decisions or take action based on the intelligence that has been provided. Feedback is also requested in order to evaluate the effectiveness of the provided intelligence. At times, the subsequent decisions and actions taken based on the intelligence provided can generate further intelligence requirements. This then initiates a new intelligence production cycle.
What is the most important phase of the intelligence cycle?
Every phase of the intelligence cycle contributes to the effectiveness of finished intelligence, but the analysis and evaluation stage holds particular importance, especially in law enforcement. Here, important details, patterns, and potential risks are examined carefully. Analysts use their skills and expertise to make sense of the data and transform it into valuable knowledge that can inform decision-making and support strategic actions.
Effective analysis can uncover hidden connections, reveal emerging trends, and provide actionable recommendations. In the case of law enforcement, it is at this stage that agencies can spot trends, identify criminal activities and take proactive measures to keep people safe.
However, the intelligence cycle is an interconnected process, and every phase, including planning, collection, processing, and dissemination, plays a vital role in the overall effectiveness and value of the produced intelligence.
Is the intelligence cycle outdated?
Critics argue that the intelligence cycle is too linear and doesn’t fit the realities of modern intelligence production. Some military commentators point out that in practice, a decision maker needs relevant intelligence to direct data collection, but the analyst can’t disseminate intelligence to the decision-maker without being directed on the data collection. The contention is that in today’s dynamic risk environment, characterised by swift changes, the conventional intelligence cycle is no longer effective.
However, technological advancements like big data analytics, artificial intelligence and machine learning have significantly enhanced the capabilities within the intelligence cycle. These advancements enable faster data processing, improved data integration and more sophisticated analysis, leading to enhanced intelligence products and insights. While the specific methods and tools used within the intelligence cycle may need to evolve and adapt over time, the fundamental principles of the intelligence cycle remain relevant and valuable in generating actionable intelligence.
How to unlock the full potential of your intelligence cycle
Silobreaker supports the full intelligence cycle with a single platform. We understand the interconnected nature of threat intelligence data, which encompasses cyber, geopolitical and physical risks. Silobreaker helps you capture and organize your Priority Intelligence Requirements (PIRs), automatically collecting relevant data from millions of sources.
This includes open sources, as well as premium sources whose data, alerts, feeds and finished intelligence reports are fully integrated into Silobreaker. Silobreaker is data source agnostic, and our customers can add their own data or data they receive from external providers.
All of these sources come together to form a single data model which the Silobreaker engine processes, translates and contextualizes the data to answer queries and meet use cases. Silobreaker provides all the tools and features you need to collaborate on, produce and share the intelligence stakeholders require, faster – all in one place.
