Based on a webinar hosted on 12 September 2023 featuring speakers David Hunt, Senior Product Manager, Silobreaker and Matthew Bey, Senior Analyst, RANE
The nexus between geopolitics and the cyber realm is a defining trend in today’s cybersecurity landscape. Whether it’s armed conflict, pandemics, elections or political agendas, all of these situations frequently set the stage for cyberattacks – opening up new avenues for cyber threat actors to capitalise on and amplify their impact.
Recent geopolitical events have sparked cyber threats, with the SiegedSec hacker group attacking the government websites of US states that have banned gender-affirming and transgender healthcare, and hacktivist group VulzSec’s cyberattack on the French National Police in retaliation for police brutality.
And as Russian and Chinese threats intensify, bolstered by artificial intelligence and upcoming elections, it’s more critical than ever that organisations integrate geopolitical intelligence into their threat intelligence programmes. The ability to monitor and understand how state sponsored groups and geopolitical dynamics impact the global cyber threats facing an organisation is essential to managing business continuity and strengthening organisational resilience.
This blog will delve into some of the key forecasts and scenarios that should be on your radar as geopolitics in conflict develops over the next few months.
Why cyberwarfare surveillance is vital for threat intelligence and decision-making
Cyberwarfare surveillance and scenario planning is essential to understand how things may evolve from the status quo. Although it’s impossible to predict with certainty what other countries and actors are preparing to do, scenario planning can be used as a way to look at the different ways an issue may develop in the near and long term.
In forecasting, even if you are highly confident in the accuracy of your assessments, the more predictions you make, the higher the probability that at least some of the assessments will be wrong. Scenario planning helps consider a range of outcomes that may affect an organisation, irrespective of whether forecasts turn out to be incorrect. For example, many analysts in the run up to the Russian invasion of Ukraine were confident that a war was unlikely. But considering scenarios of what the impact of a war in Ukraine could lead to, even if it was considered a low-probability, would have led to better-prepared responses and more effective long-term decision-making.
Assessing low-probability, high-impact incidents like these should be a part of threat intelligence and organisational planning. For example, there might only be a one in ten chance of conflict over the next 10 years that could physically impact Taiwan’s semiconductor sector. But if you are heavily reliant on Taiwan Semiconductor Manufacturing Company (TSMC), scenario planning would help reveal the potential planning actions which could be taken now to build resilience to such shocks.
Russia-Ukraine cyberattacks and future implications
When it comes to geopolitical cyber threats, Russian cyberwarfare arguably tops the list. The West – including the US and western Europe – is a prime target for different types of attacks, with motives ranging from ransomware activity that directly impacts corporations to disinformation and cyber espionage.
While Russian cyber threats have included the release of data wipers in Ukraine, this tactic has not been deployed in Western Europe or against the United States. Russia has also not been as aggressive with regard to attacking critical infrastructure in the West. This is likely due to Russia’s concern that the use of more aggressive tactics might trigger Article 5 of NATO, which states that an attack on one is an attack on all, and calls for a response.
That isn’t to say that breaches against critical infrastructure aren’t taking place, but rather that the intention might be network reconnaissance to enable future attacks versus actual disruption now.
There are several different scenarios for the Russia/Ukraine conflict going forward. The first is a best-case scenario, where Russia and Ukraine agree to reduce hostilities in the war, whether that ranges from a ceasefire to the start of negotiations to a peace settlement. In that event, we might see Russia reduce its cyber activities as an early olive branch to offer to the West. However, cyber threats overall are not necessarily going to decline.
Russia would still want to have a cyber threat lever that it can pull when needed and as a tool they can use in negotiations. It may simply mean less risk of more destructive cyber incidents, but an increase in targeted risks, such as the financial risks associated with ransomware.
The second scenario is what happens if there are significant Russian losses in Ukraine, triggering Russia to be more aggressive in its cyber activity against the West. This could include efforts to disrupt US critical infrastructure despite the risk of triggering an Article 5 response. There might also be an increase in state-backed ransomware attacks that target Industrial Control System (ICS) infrastructure. Using the cybercrime ecosystem is a way to disrupt critical infrastructure without prompting a US or NATO response due to the lack of a clear evidentiary line back to Russia.
On the other hand, if there is a widespread perception that a NATO/Russia war is highly likely, Russia might take a first-strike advantage, such as targeting a Western port or economic infrastructure, without relying on cybercrime or hacktivism as a cover for those attacks.
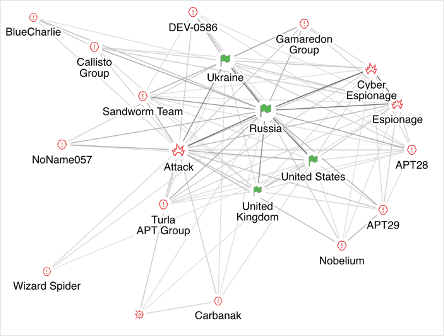
The last scenario is one that depends on Russia’s effectiveness at adopting generative AI in its information campaigns. It’s likely there will be misinformation campaigns in the US elections, and to a lesser extent, the European parliamentary elections that are coming up next year. However, the weaponisation of the cyber domain will be much more of a domestic activity, though Russia is likely to play a role in it. This could include Russia succeeding at allowing or enabling far-right voices to be heard in the mainstream.
China’s cyberattacks and future risk
China cyberwarfare stands out due to its distinct focus on espionage, with a strong emphasis on both industrial and political espionage. Notably, China considers espionage, intelligence, corporate espionage, and industrial trade secrets as interconnected elements.
The West has largely separated political intelligence from economic intelligence, but China believes that targeting Western companies for trade secrets is fair game. China also dabbles in misinformation campaigns and financially motivated attacks, but they aren’t the mainstay of China’s cyber activity.
In terms of China cyber hacking, the country has also probed Western critical infrastructure, but is much more risk averse than Russia due to its economic interdependence with the West. China would be much more affected by Western sanctions than Russia ever would be, and that limits its willingness to engage in more aggressive activities.
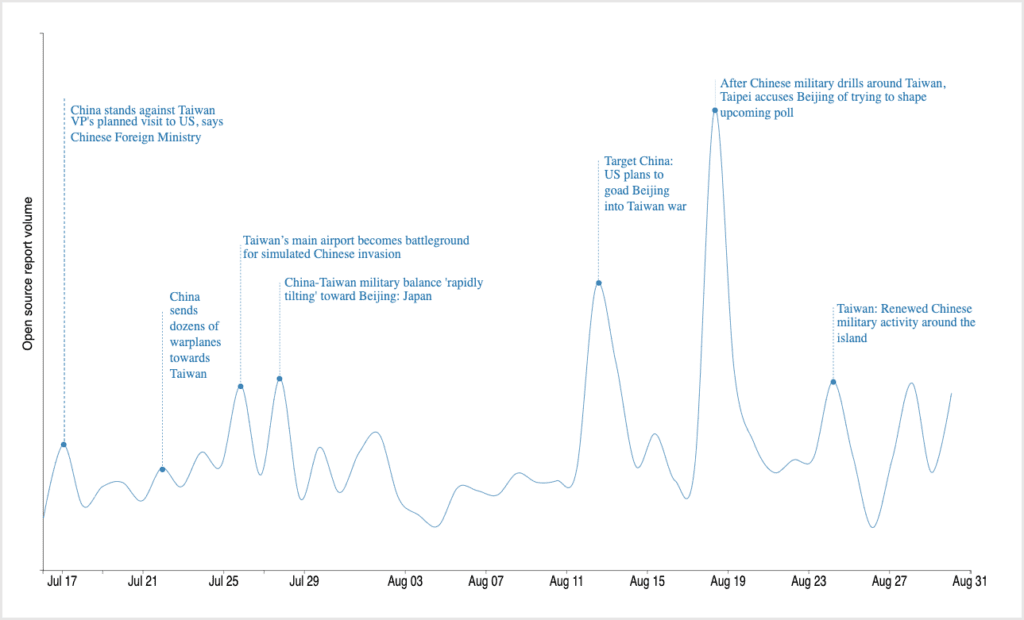
As compared to Russia, there isn’t one particular trigger for various cybersecurity scenarios, but rather a series of events that could lead to four possible consequences. The first of these is China being disruptive in industrial cybersecurity due to a substantial US/Taiwan defence agreement. This could lead to increased cyber activities like data wiper attacks, data encryption and malware, which are typically associated with Russia in Ukraine. There would also likely be a substantial regional disinformation campaign in places like Taiwan, Vietnam, Japan or South Korea where China might have more cultural affinities that allow it to be more effective.
Likewise, if a strong pro-sovereignty Taiwanese government is elected in the Taiwanese 2024 election, this could trigger a scaled escalation scenario, where China’s information campaigns target Chinese-American and other Chinese diasporas and launch more disruptive campaigns.
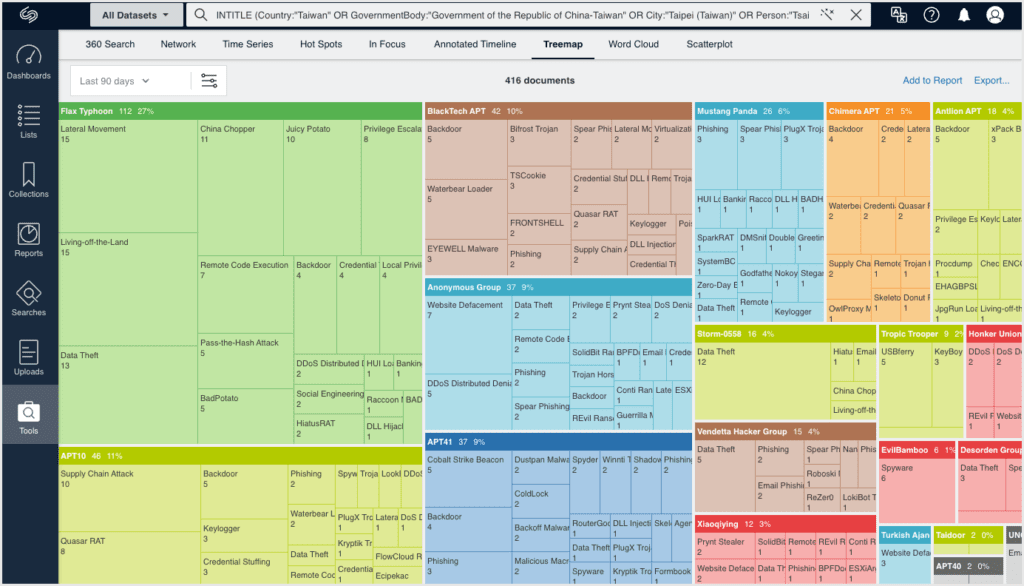
The last two scenarios are less probable but higher impact. The first being that China effectively just copies Russia and adopts a hybrid warfare strategy against the US, which includes unleashing financially motivated threat actors that have a degree of affiliation with the state. This would mean an increase in ransomware gangs linked to China that could attack Western companies the same way that Russian ones do now. However, with a much larger population, China would be more concerned about their ability to actually manage or control these organisations, and the danger that financially motivated hackers start targeting Chinese companies.
The remaining scenario is that the threat level lessens because US/China cyber cooperation increases. An example of this is the Obama era cybersecurity agreement in 2016 between China and the US, where they agreed to reduce cyber espionage, which led to a brief hiatus in cyber activities. However, while this could lead to intellectual property threats declining a bit, it would likely only be temporary and not a panacea over the long term.
Overall, there is a growing expectation of more aggressive cyber activities by China against US companies. This includes not only traditional cyber threats but also attacks on organisations across various sectors, including consumer-facing industries like retail or food, as a response to US policies.
Geopolitics and cyber threats: Strategies and tools for preparedness
Given the significant increase in state and non-state actors launching cyberattacks to further geopolitical objectives, a heightened awareness of the intersection between geopolitics and cybersecurity has become crucial. Even if Russia or China-linked threat actors aren’t in your organisation’s sights today, those dynamics could change depending on how global politics plays out over the next few months or years.
There are many different paths leading to cyberattack from Russia, China or other nation-state actors and they may involve different tactics, targets, intensities and techniques than before.
To effectively navigate this landscape, it is essential for threat intelligence teams to integrate geopolitical, as well as physical security, risk considerations into their workflows. This involves collaborating with stakeholders to identify priority intelligence requirements (PIRs), and developing structured intelligence collection plans.
The Silobreaker threat intelligence platform helps organisations formulate better questions and understand the context of geopolitical events and their link to economic stability, operations, supply chain, people and assets. This allows users to combine trusted intelligence, proprietary analysis and forecasting from RANE with open-source and technical threat intelligence content from Silobreaker to gain objective insights, and model what-if scenarios needed for strategic decision-making in one platform. Analyst teams can get ahead of the news cycle with access to more intelligence sources in one place, automated entity detection relevant to your operations and integrated analysis and dissemination tools.
Geopolitical threats aren’t going away but by adopting these strategies and utilising the right tools, your organisation can better prepare for the threats on the horizon, and enhance its resilience and readiness to respond when those threats materialise.
Watch the full webinar on-demand here.

