What is External Threat Intelligence?
External threat intelligence involves gathering and analyzing data from sources outside of an organization’s network to understand cyber threats and vulnerabilities. It helps organizations anticipate threats, strengthen their defenses and respond to incidents.
The intelligence produced using external data helps companies understand the broader threat landscape, from asset-monitoring, third-party risk management, ransomware and vulnerability intelligence, as well as the influence on cyber intelligence by geopolitics, physical security and global events.
Sources for external threat intelligence
External threat intelligence is drawn from a wide range of sources. This includes:
- Open-Source Intelligence (OSINT) – Publicly available data such as security blogs and research, vulnerability databases (e.g., CVE/NVD), government advisories (e.g., NCSC, CISA), paste sites, code repositories, social media, and forums
- Commercial threat intelligence feeds – Subscription-based services provided by specialized cybersecurity companies that offer a continuous, curated stream of information about cyber threats
- Dark web and deep web monitoring – Intelligence from hidden forums and marketplaces where threat actors trade tools, data and services
- Information sharing communities – Sector-specific or cross-industry groups that share threat intelligence and best practices (e.g., FS-ISAC, CISP)
- Government and law enforcement – Alerts, technical bulletins and collaborative intelligence from national cybersecurity agencies and law enforcement operations
Internal vs. external threat intelligence
When the term “threat intelligence” is used without any qualifier, it often refers to internal threat intelligence gathered from within an organization’s own network, systems and applications. It provides a specific view of the risks unique to a particular organization. This includes its network logs, security alerts, vulnerability scans, threat hunting findings and user behavior analytics.
External threat intelligence is the information gathered from outside an organization’s perimeter. The focus is to understand external adversaries so organizations can anticipate and defend against attacks before they happen. The core difference between internal and external intelligence is the source of data and its scope.
Importance of having both internal and external threat intelligence
Having both internal and external threat intelligence is essential for building a complete and effective cybersecurity strategy.
External intelligence provides a big-picture view of global threats, including which adversaries are active and why, as well as what tactics they’re using. This forward-looking view helps organizations anticipate attacks and build defenses against emerging threats. It also provides crucial context to determine which alerts and vulnerabilities should be prioritized.
Internal intelligence, on the other hand, reveals exactly what is happening within an organization’s own network through logs and alerts, user behavior and system activity. It can reveal actual vulnerabilities, active compromises and insider threats.
Together, they create a complete security picture. External intelligence provides context that helps organizations interpret internal alerts, distinguishing between harmless irregularities and signs of targeted attacks. Internal intelligence validates whether external threats are relevant to an organization and actively affect their systems.
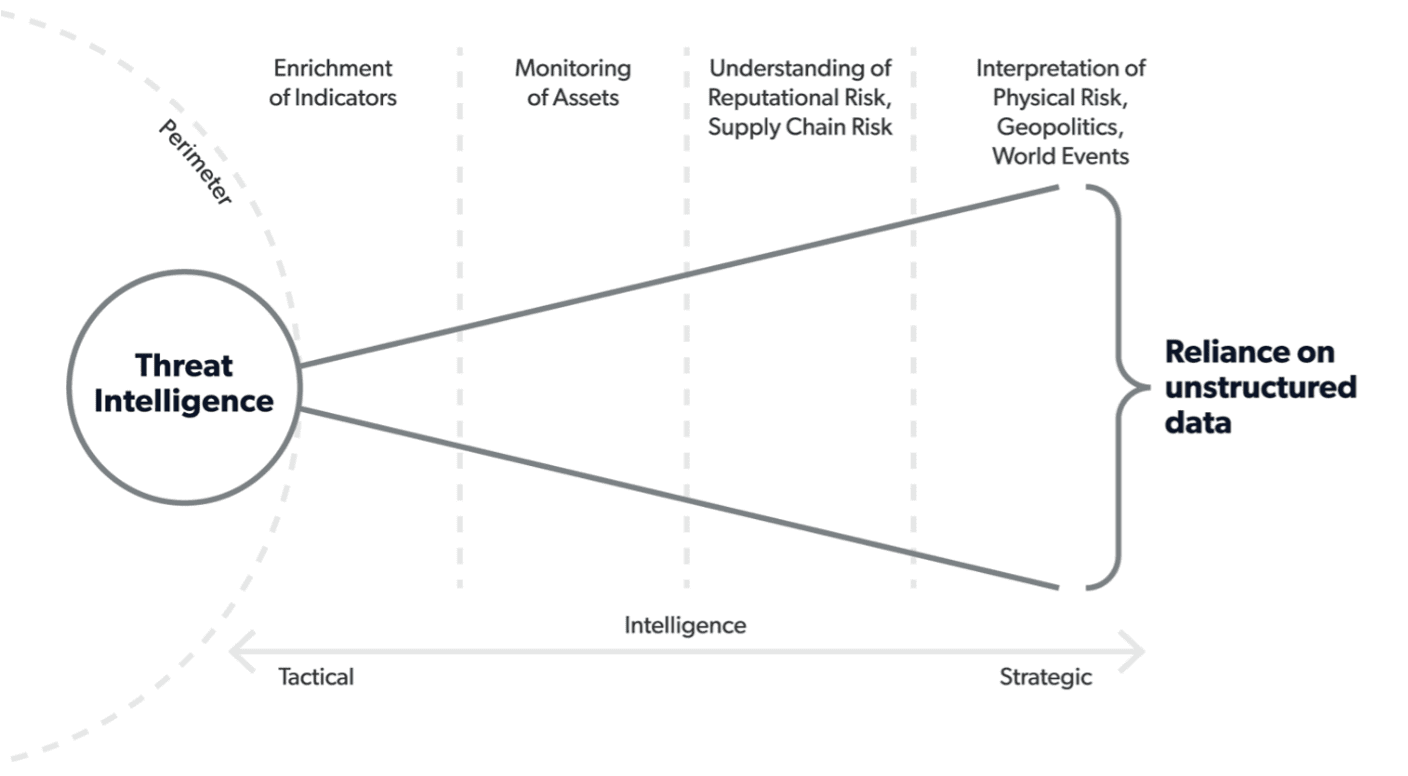
Types of external threat intelligence: strategic, tactical, operational
Threat intelligence typically falls into three categories, each providing a different level of detail and serving a distinct audience.
Strategic threat intelligence offers a high-level view of risk for executives and decision-makers, helping them understand who adversaries are, why their organization might be targeted and the long-term risks and trends that could impact the organization. This can include wider trends, geopolitical risks and industry-specific threats.
Operational threat intelligence delves into specific threat actor campaigns for threat hunters, incident responders and security managers. It provides contextualized information about threat actor profiles and their Tactics, Techniques, and Procedures (TTPs). This aids in developing threat hunting playbooks, understanding ongoing incidents and prioritizing vulnerabilities.
Tactical threat intelligence focuses on the methods and tools attackers use, such as Indicators of Compromise like malicious IP addresses or file hashes, enabling security analysts and automated tools to detect and block threats right now. This type of intelligence moves from the big picture view that strategic intelligence provides to a more granular, detailed one.
Together, these categories of external threat intelligence provide a comprehensive view of external threats, from broad trends to immediate dangers.
Silobreaker for external threat intelligence
The Silobreaker Intelligence Platform is built to make sense of text-heavy, unstructured data from external sources. Silobreaker sets the standard for external threat intelligence services, covering every stage of the intelligence lifecycle, from data collection to analysis, reporting and dissemination.
Silobreaker collects data from millions of sources across the open, deep and dark web, as well as premium providers – teaming up the best available data partners, whose content, alerts, feeds and finished intelligence reports are fully integrated into Silobreaker. Silobreaker also manages IOCs and other technical data from structured threat feeds. Customers can add their own data, or data they receive from external providers. The platform is source-agnostic and built on over a decade of curating the most relevant open and commercial content.
Manage your priority intelligence requirements (PIRs) across multiple use cases, streamlining workflows and aligning intelligence production with stakeholder needs. Analysts can query, summarize, analyze, visualize, and interpret data within a single, intuitive interface – producing high-quality, branded reports directly in the platform.
Dissemination is equally flexible, with options ranging from stakeholder alerts to automated system-to-system integrations via pre-built connectors and APIs. By unifying the entire intelligence lifecycle from collection to dissemination, Silobreaker reduces integration costs, improves data quality and enhances analyst productivity. The result is faster, more scalable intelligence production that augments human analysis and empowers better-informed decisions across the organization.
