Intelligence strengthens resilience. Thousands of cyberattacks and data breaches occur every day, and it’s more important than ever for organisations to understand the risks they face, anticipate potential threats and arm themselves with the intelligence needed to address them.

Adapt to a changing threat landscape
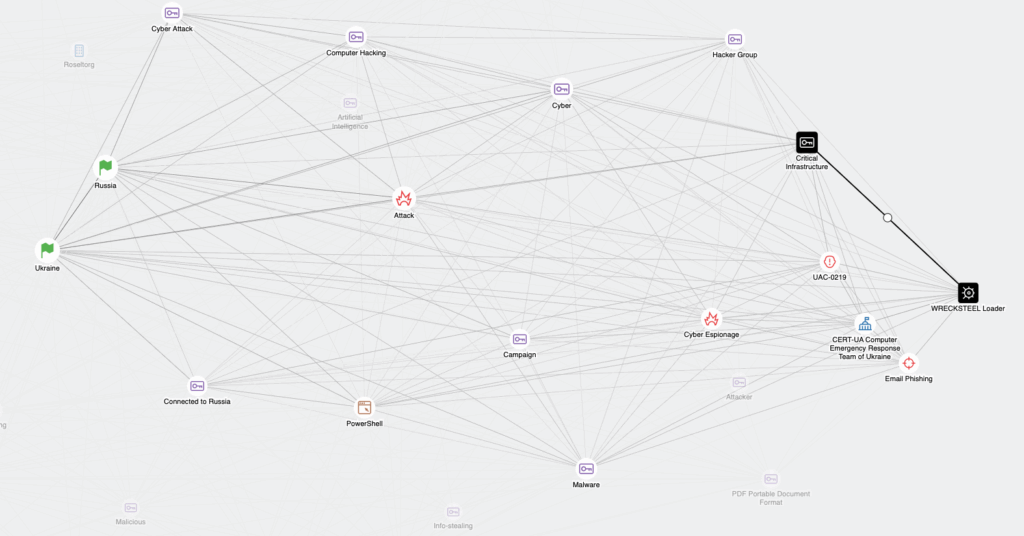
Leverage robust threat intelligence research, deep context and timely reporting in a single platform. By aggregating real-time data on threat actors, malware, active campaigns and TTPs, your team will gain a comprehensive understanding of the emerging threats to your organisation.
Capabilities
Unrivalled visibility across millions of OSINT and dark web sources in near real-time
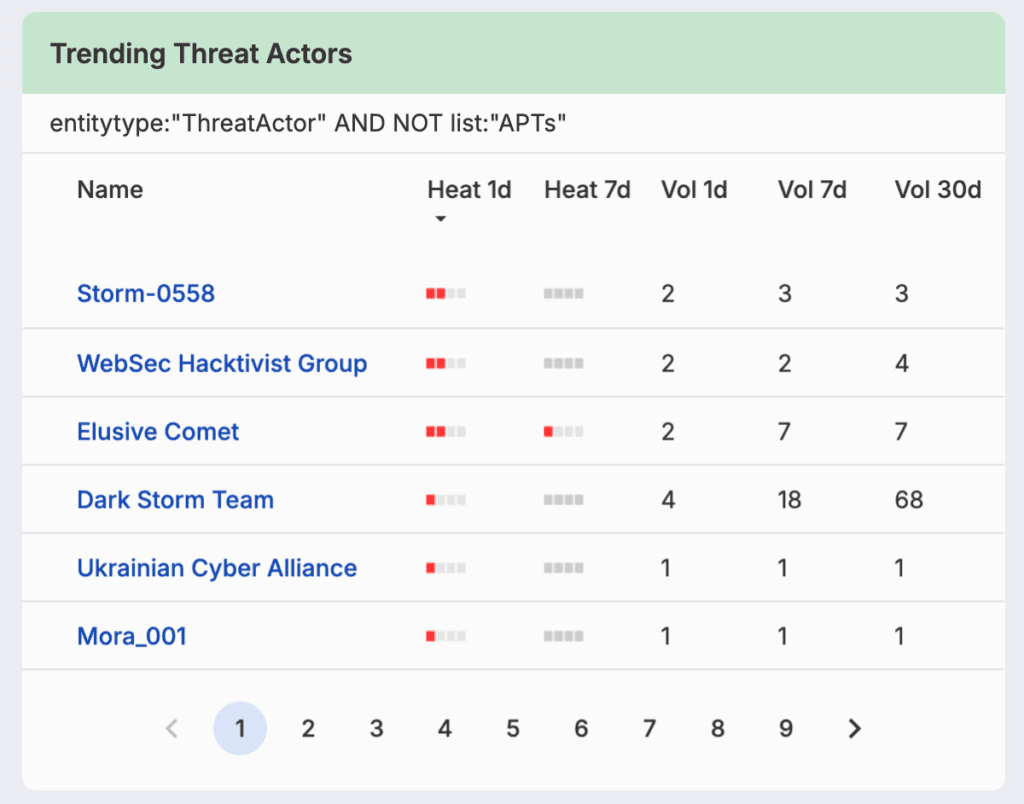
Comprehensive data on global threat actors and their evolving TTPs
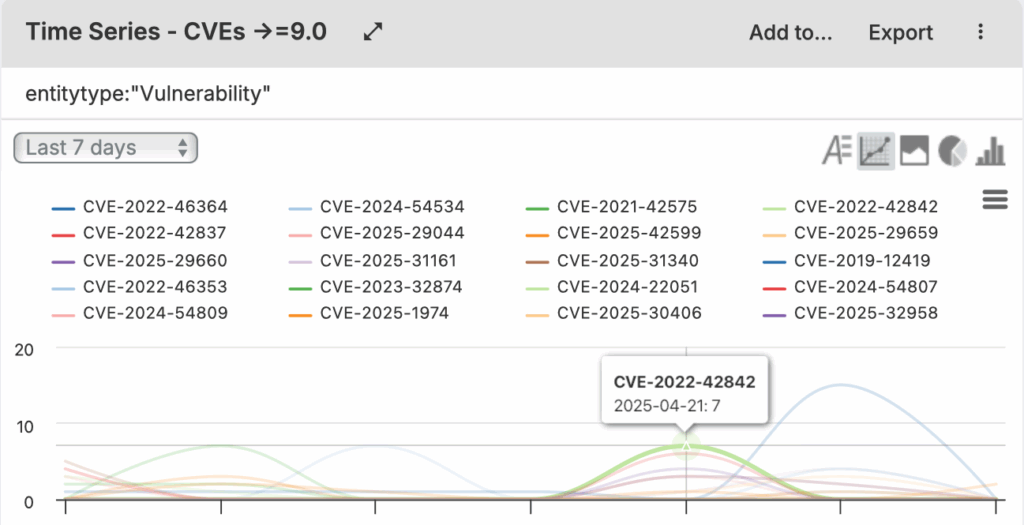
Vulnerability assessments tailored to your unique tech stack
Finished intelligence reports and daily summaries on actors and events
AI-enhanced report building and customisable alerting for key stakeholders
MITRE ATT&CK Navigator export from Silobreaker to categorise, assess and respond to threats
Deliver actionable cyber threat intelligence
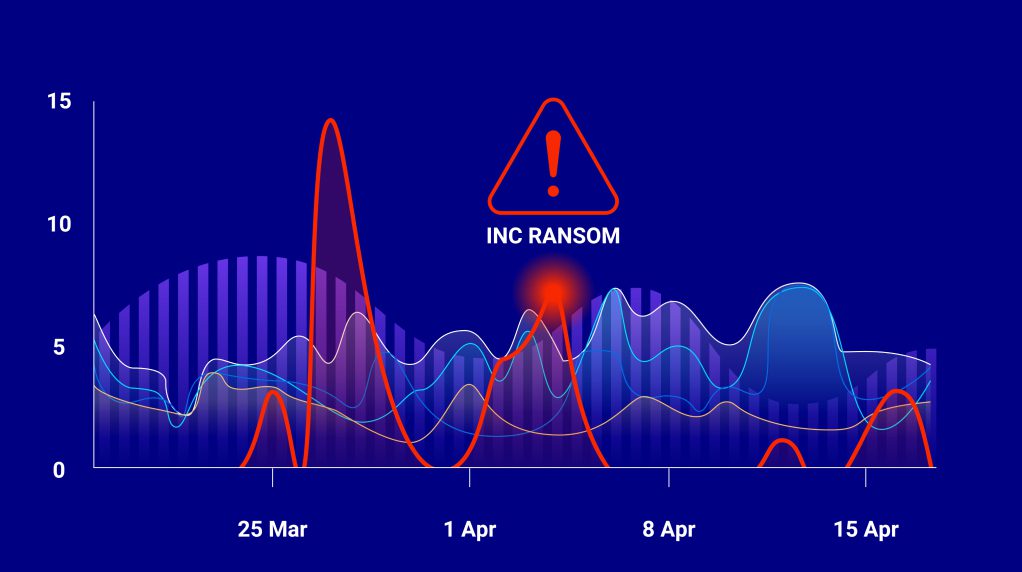
Ransomware Intelligence
Identify ransomware targeting your organisation or industry, profile threat actors, attack types and TTPs to deliver actionable intelligence.
Phishing Intelligence
Detect phishing campaigns targeting your organisation, employees or customers with contextual analysis of threat actors, domains and infrastructure, so you can eliminate threats.
Data Breaches
Be ready to respond when data breaches happen and monitor for third party breaches that could impact your supply chain due to malware, ransomware and DDoS attacks.
Stop cyberattacks before they happen
Find your top cyberattacks and data breach risks with a Silobreaker demo today.