In the ever-evolving world of cyber risk, staying ahead of threats isn’t just an ambition. It’s a necessity for organisations aiming to safeguard their digital assets and maintain operational resilience. As cyber threats become increasingly sophisticated, the need for enhanced capabilities in threat detection, investigation and response has never been more urgent.
Identifying potential threats at an early stage is critical for preventing cyberattacks and minimising their impact. And, with improved investigation tools, organisations can quickly understand the nature and scope of potential cyber threats.
This knowledge is essential for developing effective response strategies, minimising the impact of an incident, maintaining operational continuity and preventing its escalation. By swiftly neutralising or mitigating threats, organisations can avoid disruptions to their systems, services and overall business operations.
In this blog, we delve into the critical importance of advanced threat intelligence tools and how they play a pivotal role in navigating the cyber landscape with confidence. To enhance Silobreaker’s threat intelligence capabilities even further, we’re proud to announce the integration of Microsoft Defender Threat Intelligence (MDTI) into the platform.
Silobreaker + Microsoft Defender Threat Intelligence enrichment
Silobreaker’s single, customisable platform collects, processes and analyses data on cyber, physical, and geopolitical threats to improve your threat detection, investigation and incident response capabilities. With the recent addition of an advanced AI (Artificial Intelligence) tool, Silobreaker has enhanced its threat intelligence offerings, incorporating computer-aided learning and automation techniques for even more streamlined operations.
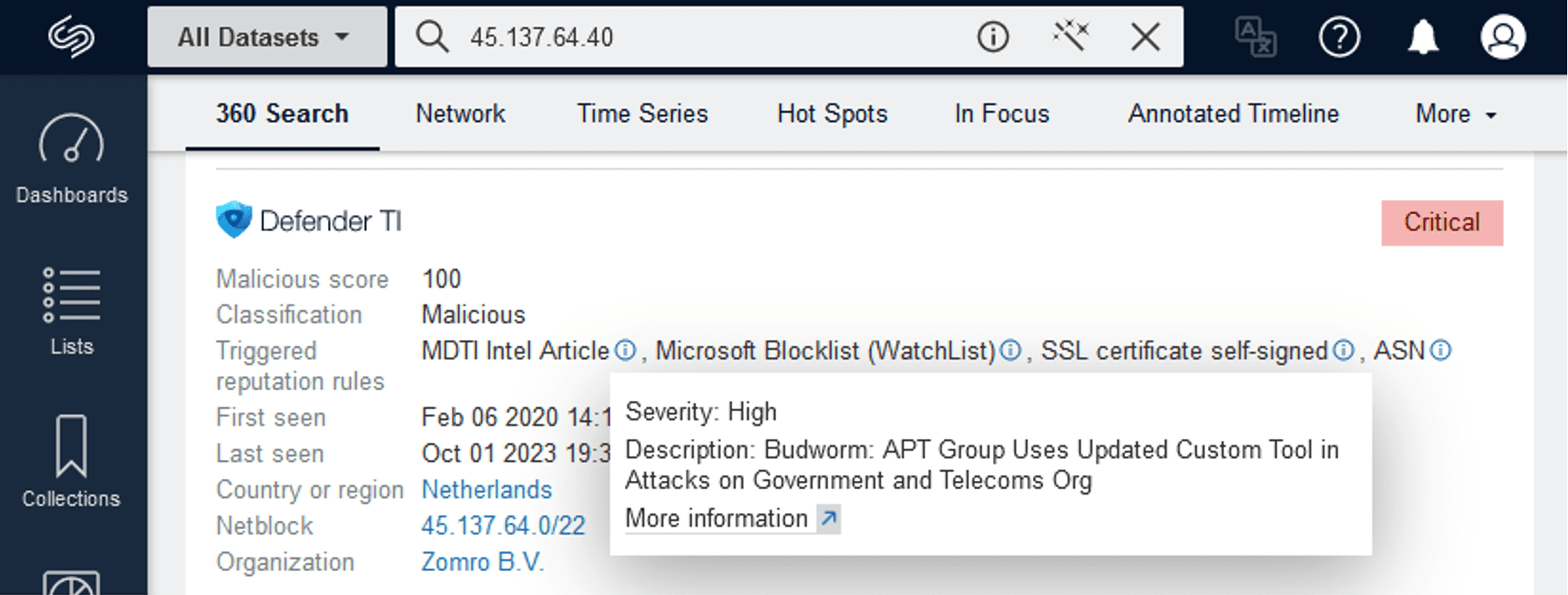
Now, the addition of the Microsoft Defender Threat Intelligence (MDTI) enrichment empowers security teams even further, providing customers with access to Microsoft’s vast repository of indicator data for domains, subdomains, and IP addresses. It also provides quick summary information about the activity of these entities, including first and last-seen timestamps, domain information, a malicious score, and a pivot to any corresponding MDTI reporting. The integration of MDTI into Silobreaker allows users to experience Microsoft Defender’s rich reputation scoring against Indicators of Compromise (IOCs), specifically IP addresses and domains, using Silobreaker’s 360 Search.
MDTI’s reputation feature assesses raw and refined threat intelligence – using Microsoft’s internet intelligence graph, machine learning algorithms, and a network of over 8,500 cybersecurity researchers – and categorises IOCs along a spectrum from good to bad. Silobreaker enhances this feature by generating a normalised score for IOCs based on risk assessments from various third-party sources like VirusTotal, Domain Tools, Threat Fox, URLhaus and now MDTI.
These reputation scores swiftly report the level of confidence that IOCs identified in the network data are associated with known threats and pose a potential risk or harm. This confirmation helps organisations prioritise incidents, make decisions on how to respond, and even automate actions to contain the threat.
Benefits of Microsoft Defender Threat Intelligence integration
The Silobreaker + MDTI enrichment integration offers several benefits to security teams:
- Increased confidence in reputation/risk scores: Silobreaker normalises the Microsoft rating alongside other enrichments, providing a unified risk score for more confident decision-making.
- Improved efficiency: Eliminates the need to compare and analyse risk scores from different sources, saving time and resources.
- Deeper context and insights: Provides additional context and insights into IOCs, including Advanced Persistent Threat (APT) groups linked to malicious infrastructure and associated tactics, techniques, and procedures (TTPs). This information can initiate threat investigations, assist in the hunt for threats across the network and log files, and help organisations better understand threat actor TTPs.
How to use the Microsoft Defender Threat Intelligence Enrichment
The Microsoft Defender Threat Intelligence enrichment can be used in a wide variety of security roles and use cases.
Incident Responders
Incident responders can use the Microsoft Defender Threat Intelligence enrichment to quickly validate the reputation of IOCs detected in telemetry from the network. This information can be used to prioritise incidents, make decisions about how to respond and automate containment actions.
Threat Hunters
Threat hunters can use the Microsoft Defender Threat Intelligence enrichment to initiate threat investigations and hunt for threats across the network and in log files. The additional context and insights provided by Silobreaker can help threat hunters to better understand the tactics and techniques of threat actors and potential attacks before they cause damage.
Example Use Cases
Some real-life examples demonstrating the practical application of Microsoft Defender Threat Intelligence enrichment include:
- Security response team: The security incident response team receives an alert about a suspicious domain detected in network traffic. They use the Microsoft Defender Threat Intelligence enrichment to validate the reputation of the domain and learn that it is associated with a known malware campaign. The team then blocks the domain and quarantines any infected hosts.
- Threat intelligence analyst: A threat hunter is investigating a recent phishing campaign. The threat hunter uses the Microsoft Defender Threat Intelligence enrichment to identify the malicious infrastructure used in the campaign. They then hunt for this infrastructure across the network and in log files. The infrastructure is found on several hosts and steps are taken to remove it.
Enhance your cybersecurity strategy
From earlier threat identification, to minimising attacker dwell time in your network and faster response to threats, Silobreaker’s threat intelligence platform empowers your cybersecurity teams and provides demonstrable ROI (Return on Investment) to senior leaders.
Silobreaker’s latest integration with the Microsoft Defender Threat Intelligence enrichment provides increased confidence in reputation/risk scores, improved efficiency, and deeper context and insights, enabling your organisation to make informed decisions and respond effectively to threats.
If you are looking for a way to improve your threat hunting and investigation capabilities, Silobreaker’s Microsoft Defender Threat Intelligence enrichment integration is a valuable solution.
Contact Silobreaker today and request a demo to learn more.

