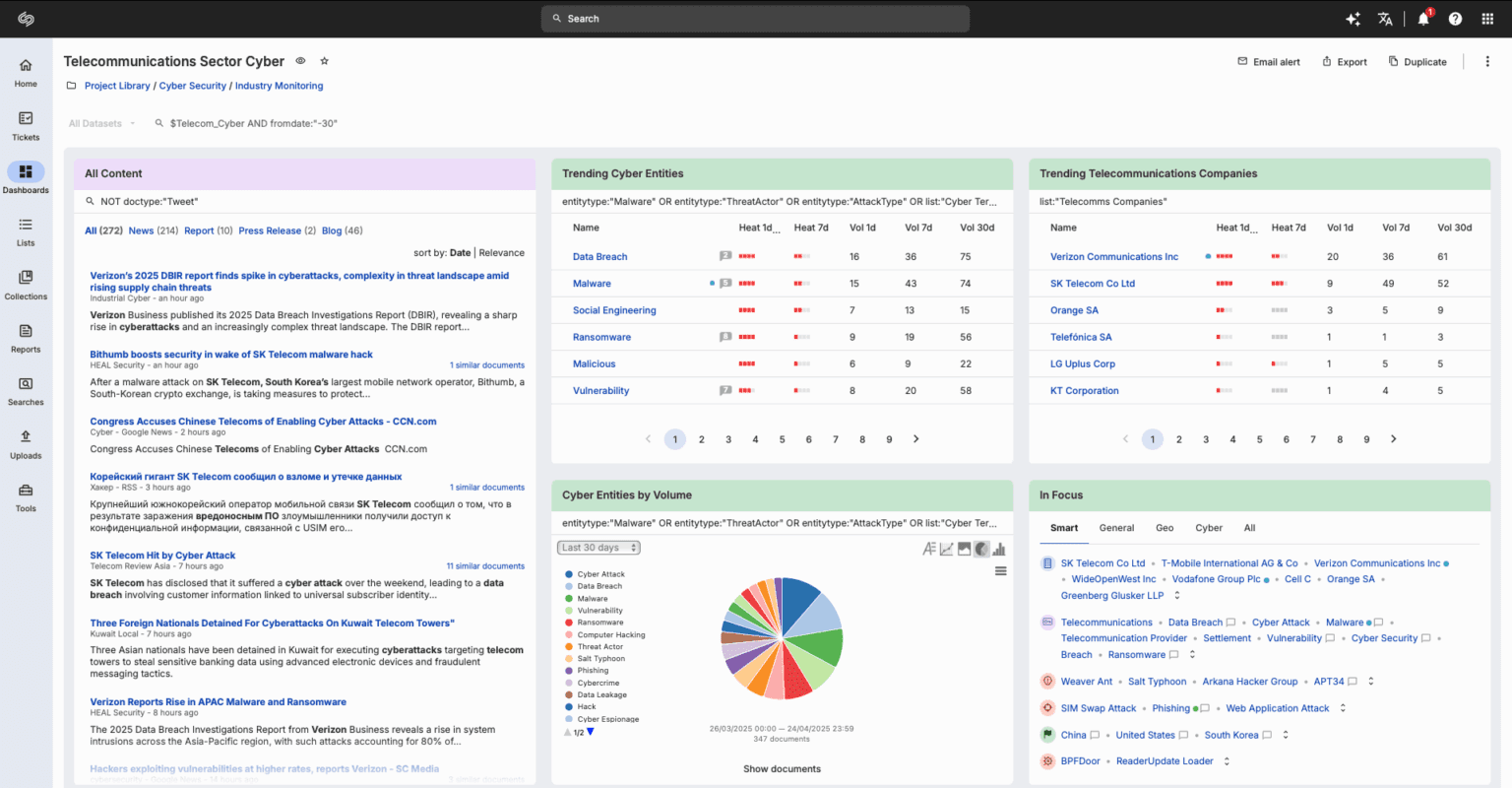
Understand and mitigate risks to safeguard sensitive data, intellectual property, products and other business assets. Monitor cyber, geopolitical and physical threats and keep up to date with the fast-paced, dynamic environment in which your organisation operates.


Stay ahead of threats targeting your business and operations
Through Silobreaker, produce timely threat intelligence as the threat landscape evolves and new vulnerabilities emerge. Monitor threat actors, campaigns, malware variants, associated TTPs and IOCs. Understand the bigger picture and take a proactive approach by looking at the wider geopolitical context from which threats arise.
Safeguard sensitive data and respond to incidents faster
Automate the monitoring and alerting on leaks of sensitive data across a wide range of sources including underground channels and paste sites. Pick up on new mentions that could indicate threat actor interest and intent to target your organisation and take timely action.
Keep informed about new exploits before they become a major threat.
Using Silobreaker’s dashboard and alerting capabilities, uncover new zero-day exploits and vulnerabilities specific to your products and applications. Receive early warning to mitigate risk.
Boost your supplier risk management strategies
Gain deeper visibility into supplier cyber incidents to develop comprehensive, proactive strategies to mitigate supplier risk.
“What has previously taken weeks to research and complete, we’ve managed to finish in a single day with Silobreaker.”
Learn how business development analysts utilise Silobreaker to automatically aggregate data around niche technology markets to uncover relationships and find strategic advantages in developing sectors.

Technology Manufacturer Unlocks Market Intelligence To Gain Business Advantage
ViewGain a comprehensive understanding of threats to your operations
Start tracking emerging and evolving threats today to enable decision-makers to better manage and mitigate risks to your organisation.