Significant number of ransomware attacks reported in H1 2023
Ransomware continues to be a hot topic among cybersecurity researchers, with attacks having continued at a high pace throughout the first half of 2023. When compared to the Ransomware? What Ransomware? findings from 2022, the figures are almost shocking: whereas we analysed a total of 430 publicly reported ransomware attacks in 2022, we identified the same amount of publicly reported ransomware attacks in H1 2023 alone.
While such a high number in the first six months of 2023 may be due to the reporting of ransomware attacks having improved over the past half year, security researchers have also observed an increase in attacks more generally. Ransomware attacks appear to remain a very lucrative business model for many cybercriminals, despite the fact that victims are generally advised not to pay ransoms.
Overview of statistics
| All findings are based on available data on the Silobreaker platform, with reports written by the Silobreaker Analyst Team as a starting point for the initial public reporting. Some limitations of this include that the focus is strictly on English reporting. More details on the methodology can be found in the 2022 Ransomware? What Ransomware? Report. |
In the first half of 2023, we observed 437 victims, seven of which denied that an attack took place, or prevented the attack from being successful. Of the remaining 430 victims, six were targeted in potential or suspected ransomware attacks, while three received an apology and a decryptor from the threat actor after being targeted.
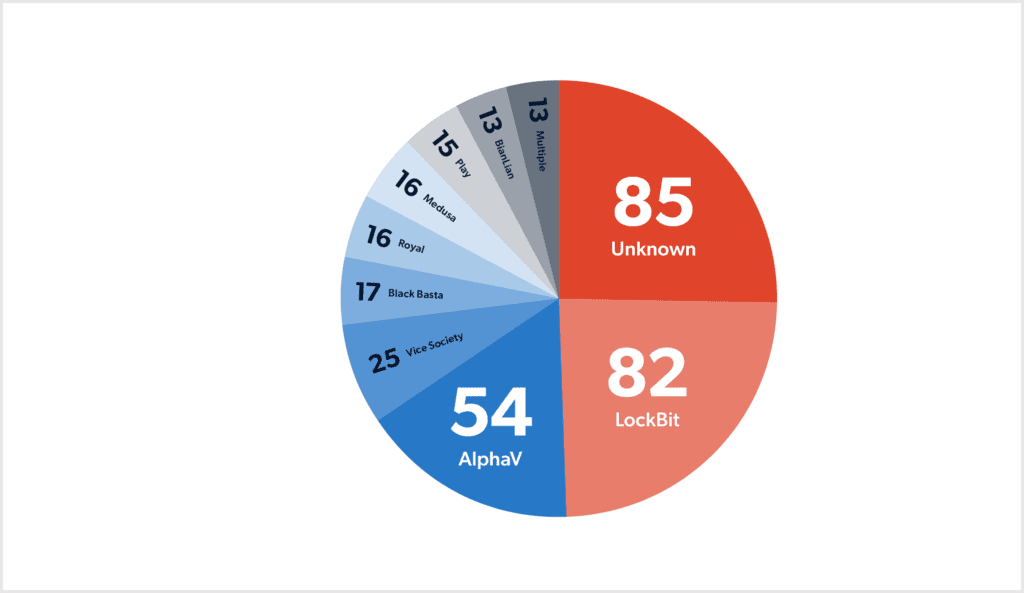
When taking Clop ransomware’s attack against MOVEit Transfer into account, the group was by far the most active ransomware group in the period. Separate from the group’s attack against MOVEit Transfer, Clop only claimed a few victims. The other most active groups were LockBit with 82 victims, AlphV with 54, and Vice Society with 25. This follows last year’s trend, which saw LockBit, Hive, AlphV and Vice Society at the top, although Hive has only claimed three victims so far in 2023.
Out of all attacks, 85 were carried out by unknown threat actors. For 13 of the victims, multiple known ransomware groups claimed responsibility for the attack. In these cases, it is unclear whether the victim was targeted more than once, or if there is any connection between the groups and their claimed victims.
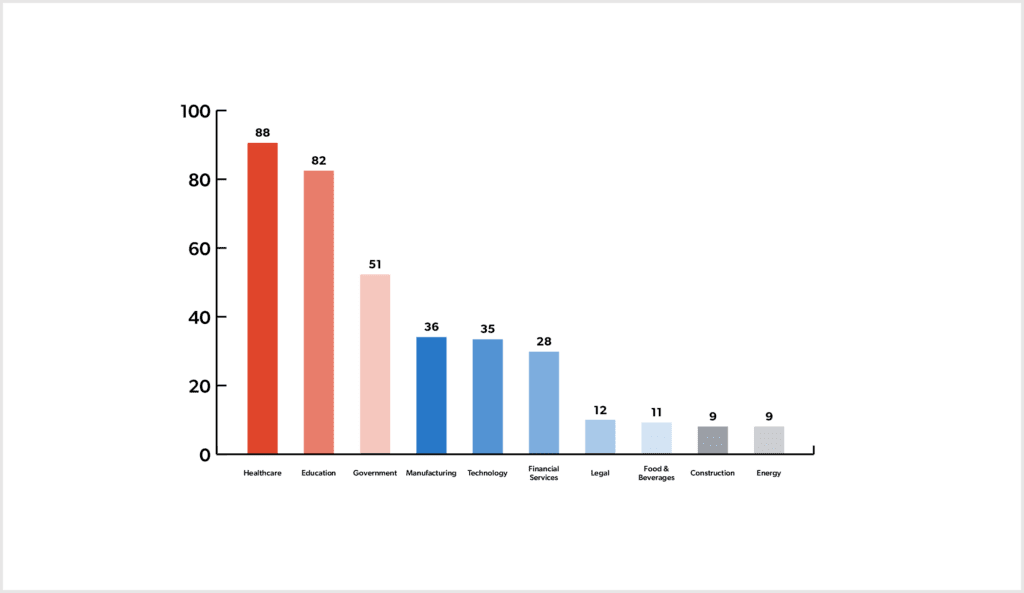
H1 2023 saw the healthcare sector targeted the most, with a total of 88 victims observed. The other most targeted sectors were education, government, manufacturing and technology. This reflects last year’s trends, which saw the healthcare sector targeted the most, followed by government, education, technology and manufacturing.
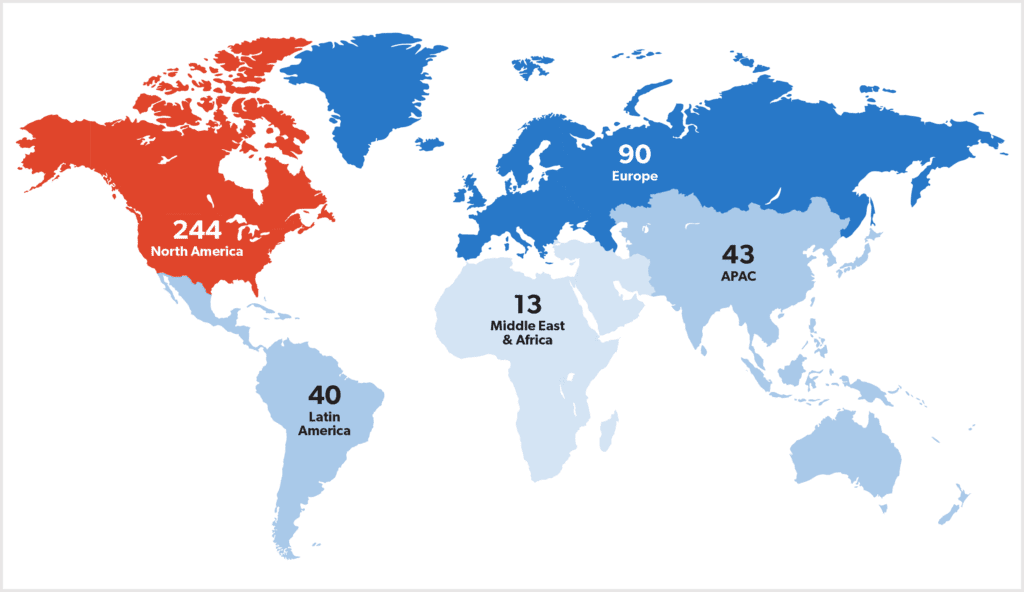
The most targeted world region was North America, with the United States suffering 230 attacks and Canada 14 attacks. This was followed by Europe, Asia Pacific, Latin America, the Middle East and Africa with 13. This is similar to last year’s findings, which saw Western countries targeted more frequently than others.
Continuing last year’s trend, there was a far higher number of victims listed on the deep and dark web by ransomware groups, compared to publicly reported ransomware attacks. Specifically, over 2,000 victims were listed on such sites, indicating that there continues to be a huge blind spot in the coverage of ransomware attacks in public reporting.
Mass exploitation campaigns
Not only has the first half of 2023 seen a major increase in publicly reported ransomware attacks, but it has also been marred by several mass exploitation campaigns by ransomware actors. Two of these campaigns were carried out by the Clop ransomware group, who have been making a name for themselves in the ransomware threat landscape as a threat actor that carries out supply chain attacks to cause the biggest impact. Each of the campaigns described below saw the exploitation of a specific vulnerability in a targeted product – a technique that appears to have become more popular among threat actors in recent months.
Similar to other ransomware attacks against organisations that may have a trickle-down effect to other organisations, the vendor of the affected product is considered the victim organisation in our database collection, while the companies who had their data stolen are seen as victims of the supply chain. This means that the individual victim organisations affected by the campaigns described below have been excluded from our general statistics.
MOVEit Transfer
The most recent of these mass exploitation campaigns targeted a vulnerability in the managed file transfer service, MOVEit Transfer. The attacks first began in late May 2023, with Clop claiming responsibility for the attack by early June 2023. As of the time of writing, over 2,000 organisations have been confirmed to be affected, with the data of over 60 million individuals compromised.
What made this specific ransomware campaign so unusual was the tactics and techniques that Clop used. The group reportedly first tested out an exploit for the vulnerability in early 2021, with the threat actors clearly aware of the major impact an attack on such a widely used product could cause. Unlike their typical attacks, no ransomware payload was used to encrypt files. Instead, Clop focused on data theft alone, with two separate data leak threats issued in June and August 2023. Not only did Clop leak the data on their dark web leak site, they also made stolen data available on clearnet sites and via torrents, with the former technique also previously used by the AlphV ransomware group. By August 15th, 2023, the second deadline given by Clop, they had released their first full data leak. This was followed by a massive data dump 15 days later, which saw a total of 229 organisations’ data dumped on Clop’s leak site.
The attack on MOVEit Transfer continues to impact organisations, with new data breach notifications issued on a daily basis. It remains unclear how many, if any, targeted organisations paid the demanded ransom.
GoAnywhere MFT
Prior to Clop’s mass exploitation of MOVEit Transfer, the group also targeted a vulnerability in a different managed file transfer service, in this case, Fortra’s GoAnywhere MFT. The number of victim organisations in this campaign is far lower compared to the MOVEit campaign, with 130 claimed victims. The group first exploited the vulnerability at the end of January 2023 and claimed responsibility for the attack by February 10th, 2023. By March 17th, 2023, Clop leaked data stolen from 60 victims. As in the case with MOVEit, it is unclear how many, if any, victim organisations paid the demanded ransom. Despite the attack having taken place in January, one of the most recent victim disclosures was made towards the end of July 2023.
ESXiArgs attacks
A curious wave of ransomware attacks began in early February 2023 that involved the so-called ESXiArgs ransomware strain. The attacks have variously been attributed to the Black Basta ransomware group and the newly emerged Nevada Group, while others state the ransomware is based on the source code of Babuk. They targeted unpatched VMware ESXi servers by exploiting a known remote code execution vulnerability that was patched in 2021. This campaign has largely been described as unsuccessful, with no data leaked from any of the reported 5,000 victim organisations.
Observed trends
Threat actors move away from encryption
More and more organisations appear to have the necessary security measures in place to prevent any encryption of data or easily recover their files. However, as was already seen in 2022, ransomware actors continue to steal data from their victim organisation prior to encrypting systems. This means that, even if the encryption payload is prevented from executing, the ransomware gang can still leverage the stolen data to extort the victim. In fact, a more recent trend is also seeing the attackers skip the encryption step completely, and instead focus solely on data exfiltration.
This trend has opened a debate surrounding the definition of ransomware actors, where technically those no longer using encrypting payloads or ransomware are merely extortionists in the simplest of terms. Nonetheless, any intrusion into an organisation’s systems can have widespread consequences, with not just proprietary data at stake, but also that of any clients that a victim organisation has. Perhaps this is why some companies choose to pay the demanded ransom, out of fear that such data will be made public.
Threat actors list multiple victims in one day
Another trend observed throughout the first half of 2023 was ransomware actors naming multiple alleged victims on their data leak site on the same day. Even when taking Clop’s victims out of the equation, there are many threat actors that have begun naming numerous victims at the same time. Take, for example, LockBit, which added a total of 24 new victims to their data leak site on June 5th, 2023. It remains unclear whether the initial attacks all took place on the same day as well.
When looking at public reporting, however, many of the alleged victims are not named. Reporters frequently list a few of the named victims but, in many cases, not all of them. When only relying on open-source reporting, this causes more of a blind spot in understanding the true figure of ransomware victims.
Many victims continue to avoid mentioning ransomware in disclosures
In 2022, we observed victim organisations increasingly referring to ransomware attacks as simple cyberattacks or IT incidents, or, in some cases, generic data breaches. From January 2023 to the end of June 2023, this trend has continued, with only 110 victim organisations mentioning ‘ransomware’ in their disclosure, while 17 organisations referred to encryption in some way or other, and five mentioned a ransom demand. This indicates that nearly 70% of victim organisations did not disclose that they had suffered a ransomware attack. As many ransomware attacks today have a wider supply chain impact, this lack of transparency could leave many customers’ data at risk, with many possibly not aware that their data was compromised.
Closing thoughts
The fact that the first half of 2023 had the same amount of publicly reported ransomware attacks as the whole of 2022 demonstrates that ransomware continues to pose a credible threat to organisations. The mass exploitation campaigns we have seen by Clop in particular show just how dangerous an attack against one entity can be for an entire supply chain. Whether such attacks will continue throughout the rest of the year remains to be seen and is dependent on ransomware actors being in possession of a zero-day exploit that will give them access to the data of thousands of organisations.
With some ransomware actors no longer focusing on encrypting data, the nature of the threat has shifted somewhat, though ransomware actors appear to continue to have success in monetising their attacks – be it by receiving their demanded ransom or selling the data to the highest bidder. Perhaps this type of trend is also why many victim organisations do not mention ransomware in their disclosures. Nonetheless, even victim organisations that had their data encrypted continue to use rather vague language in their disclosures, which may result in misunderstandings of the nature of the threat.
Learn more about how you can stay one step ahead of ransomware attacks or download the report Ransomware? What Ransomware?
