Between BlackCat’s recent exit scam and LockBit’s faltering attempt at a comeback after its takedown, two of the largest players in the ransomware-as-a-service (RaaS) ecosystem have unceremoniously been dethroned. These recent events have not only exacerbated current tensions among ransomware actors, but also begun to notably shift the way in which they operate, despite an overall increase in ransomware attacks reported throughout Q1 2024.
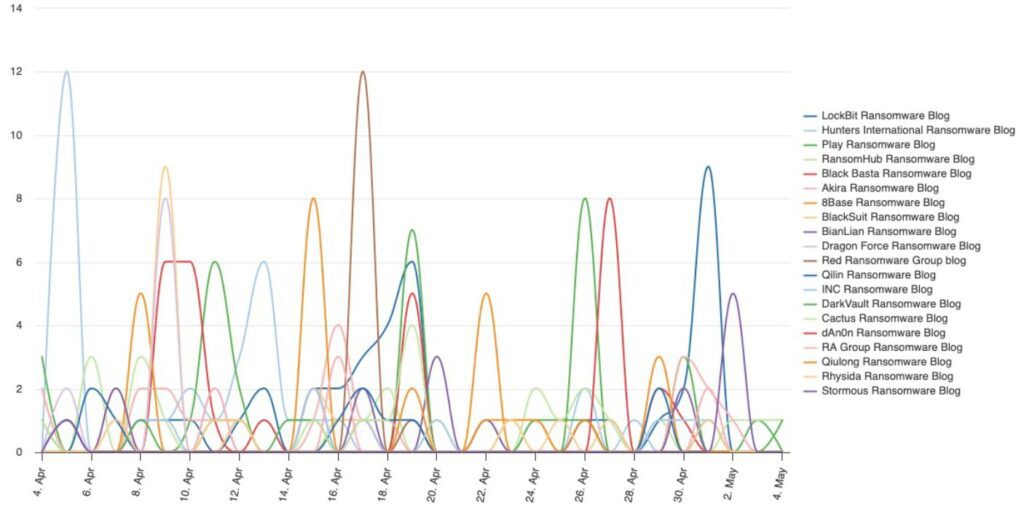
Notably, scams, successful law enforcement operations, and the development of high-profile decryptors have precipitated an undercurrent of tension and distrust in online hacker circles, which various ransomware actors have both exploited and attempted to compensate for in equal measure. Following our recent 2024 Ransomware Report, we sought to analyse these factors, their implications, and their impact on the ransomware threat landscape going forward.
Law enforcement finds recent high-profile successes
Announced on February 20th, 2024, Operation Cronos was an international law enforcement effort that resulted in the takedown of LockBit’s data leak site, various affiliate and support servers, and LockBit’s administrative panel. Two of LockBit’s operators were also arrested, with their compromised website used by law enforcement to release decryption keys and disseminate information about the group and its operations. Observations from Trend Micro showed significantly diminished LockBit activity following the event, with only one small attack cluster identified the month after. Operation Cronos was not an isolated incident, finding itself standing on the shoulders of other recent and significant ransomware takedowns, including the Hive ransomware group in January 2023 and RansomedVC in November 2023. These efforts have also often been complimented by the release of ransomware decryptors, with notable ones recently developed for Rhysida, BianLian, and Hive, as well as an updated decryptor for Babuk Locker. Operation Cronos was lauded for its hybrid approach, with law enforcement learning from the shortcomings of a prior takedown attempt targeting BlackCat in December 2023, which was only short-lived.
The reputational cost of takedown operations
Whilst physical takedowns are potentially recoverable, the reputational damages these efforts have had on ransomware actors is arguably more telling. Reputation lies at the core of successful RaaS operations, enabling threat actors to secure affiliates, successfully extort victims, and maintain key relationships in online hacker communities.
In the aftermath of Operation Cronos, LockBit’s representative, LockBitSupp, was banned from the notorious XSS and Exploit hacker forums for allegedly scamming affiliates, with multiple users jumping on the bandwagon to leverage further accusations and complaints. LockBitSupp’s ban was ultimately likened to a public execution, with the ‘Ripper’ status they were assigned marking them as a permeant pariah in hacker circles and likely impacting their ability to secure business.
Another contributor to the tension amongst online actors was speculation that LockBitSupp had worked with law enforcement – in an effort to justify how one of the most notorious ransomware players had fallen, some users rationalised that foul play had to be involved. These fears were bolstered by law enforcement releasing vague allusions to communications with LockBitSupp. Concerns about how LockBit was initially compromised also further heightened the underlying sense of paranoia amongst ransomware groups, with many, including an operator of Snatch RaaS, quickly scrambling to identify their own potential exposure.
It’s clear that the impact of Operation Cronos has had considerable effects on both LockBit’s reputation and the overall psyche of online hackers, who are both wary of law enforcement but also of ‘snitching’. A similar fallout happened following the takedown of the RansomedVC operation. The threat actor USDoD accused RansomedVC’s creator, RansomedSupport, of being a liar who collaborated with law enforcement and provided them with information that led to the arrest of RansomedVC affiliates. Both incidents show how takedowns pave the way for often damaging accusations and speculation regarding those targeted, some of which can likely be exploited by competitors seeking to displace the impacted groups. Equally, the paranoia provides ample opportunity for law enforcement to sow further distrust. Future law enforcement efforts are likely to leverage similar tactics to the LockBit takedown, leveraging strategic ambiguity to generate apprehension.
Scams, betrayals, and fraud remain rife among threat actors
BlackCat’s recent exit scam, conducted after a significant ransomware attack on Change Healthcare, demonstrates why distrust and paranoia among hackers is not entirely unfounded, with BlackCat having been touted as a reputable group and potential replacement to LockBit prior to the event. The scam, which involved BlackCat reuploading the FBI’s prior takedown notice to their leak site, also displays another novel consequence of hacker vigilance around law enforcement efforts, with the manufactured takedown leveraged by BlackCat to justify shutting down their operations and running off with affiliate money. The incident demonstrates that threat actors might attempt to weaponise the paranoia around law enforcement to heighten the believability of attempted scams, with the impact of these schemes amplified by the often intentional ambiguity accompanying legitimate takedowns. The recent success of Operation Cronos is also likely to motivate further groups to leave the ransomware ecosystem as fear begins to eclipse the material benefit of continually operating. Such a cost-benefit calculus was reportedly what encouraged the Avaddon RaaS operation to disband in 2021.
The overall prevalence of ransomware-related scams has meant that, despite the reported increase in ransomware, hackers and prospective affiliates have found themselves in somewhat of a crisis of confidence. As identified by Guidepoint Security, newer RaaS players, such as BEAST Ransomware and RANSOM FLOCKER, have accordingly sought to exploit these current circumstances in marketing themselves, presenting enticing financial incentives. The events surrounding LockBit and BlackCat, as much as they caused fear, undoubtably created a power vacuum in the RaaS ecosystem that such threat actors are attempting to capitalise upon, with newer ransomware particularly accounting for a large amount of recently observed activity.
However, such ransomware actors might also find difficulty establishing themselves against the heightened trust requirements demanded by other hackers. Newer groups seeking to establish a reputation are primarily going to rely on material incentives to compensate for their lack of established reputation. The salient concern of ransomware scams will likely mean that many newer groups will fail to consolidate affiliates in the long-term if they do not directly implement measures to address the concern of scams. One such measure being implemented has involved ransomware actors prioritising forms of professionalisation in their enterprises to distinguish themselves from scam attempts. Such groups, as Conti once did, aim to function more like regular companies, promoting the use of specialised teams, improvements to their core ransomware ‘product’, and progressive payout scales. In marketing from Medusa ransomware, the hacker group offered affiliates support from a specialised admin team, a media advertising team, and negotiators, demonstrating a level of sophistication that will likely be better for affiliate retention. Since options for professionalisation tend to be more indicative of developed operations, it will likely be mature groups that reap the ultimate benefits of current circumstances, despite the overall surge in newer ransomware groups observed.
Rebrands, variants, and brain drain keep the ecosystem ever-changing
Despite takedowns and exit scams, the ransomware ecosystem has remained both thriving and in constant flux. One factor contributing to this is the persistent use of rebrands by threat actors, which is typically employed to throw off law enforcement efforts. One emergent trend is rebrands also being used by groups that have suffered adverse controversy, enabling them to potentially start afresh in the wake of a takedown or exit scam. In April 2024, security researcher Dominic Alvieri identified a new ransomware blog, dubbed DarkVault, that had overlaps with LockBit’s old data leak site, including design choices, colour schemes, the displayed ransomware clock, and an accidental use of the LockBit logo. DarkVault could indicate a potential attempt at a comeback by LockBit’s operators in order to shake off the controversy arising from Operation Cronos.
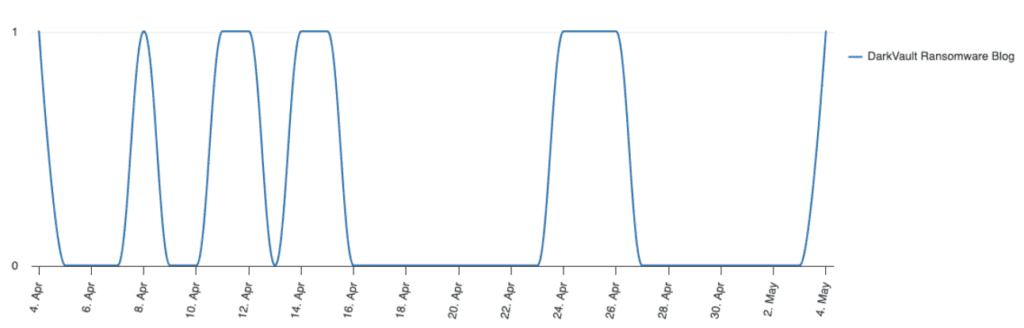
Conversely, the ease with which threat actors can rebrand opens up the possibility of imposters and potential scams. It is likely that, following the events surrounding BlackCat and LockBit, other threat actors might attempt to imitate the groups to either leverage their former reputations in pressuring victims, or to facilitate sophisticated scams. The leaked LockBit Black builder will also make it easier to add authenticity to any impersonation attempts involving LockBit in particular. Multiple ransomware strains have already been observed leveraging LockBit Black’s source code, enabling them to potentially benefit from LockBit’s reputation when extorting victims. These ransomware variants include Buhti, Wing, Bl00dy, and DragonForce.
One other factor contributing to the overall fluidity and long-term resilience of the ransomware ecosystem is that talent also often persists and shifts between groups. RedSense’s Yelisey Bohuslavskiy identified that penetration testers previously affiliated with Conti shifted their efforts from LockBit to the Akira ransomware group after Operation Cronos. Prior to this, LockBit themselves reportedly poached talent from BlackCat and NoEscape following disruptions against the former and the closure of the latter. Relatedly, the RaaS model means that affiliates are often able to jump ship following disruptions to an operation, taking information from their victims with them. As an example, Trellix assess that the Werewolves ransomware gang likely consists of former LockBit affiliates, with many listed LockBit targets also appearing on the Werewolves blog, either having been moved there or targeted once again. This shows that top-tier talent is often able to persist through infrastructure disruptions and remain resilient, contributing to the continued persistence of ransomware despite successful takedowns.
Final Thoughts. Somehow, ransomware returned
Moving forward, threat actors are likely to try various means to address the ongoing lack of confidence in RaaS enterprises, with recent events surrounding LockBit and BlackCat having had a clear psychological impact on the online ecosystem. These same events are likely to be exploited by other actors to further their own agendas, be it those seeking to establish their own reputations or facilitate scams for short-term gain.
The overarching fear of scams and exit schemes is likely to remain prevalent among ransomware actors, especially following BlackCat’s dramatic departure. Heightened countermeasures and scepticism on online hacker forums will likely escalate, presenting a higher barrier of entry for newer groups compared to those that are already established.
The overall resilience of the ransomware ecosystem means that, whilst the incidents surrounding LockBit and BlackCat were significant victories, they are unlikely to change ransomware’s overall prevalence in the long-term. Affiliates and experienced hackers will remain resilient to takedowns, shifting their activity between groups to continue operating. Ransomware groups will also likely continue to leverage rebrands in order to evade law enforcement and persist after supposed exits. LockBitBlack’s leaked builder will particularly afford new groups the unique opportunity to benefit from LockBit’s former infamy, facilitating potential impersonations and extortion attempts. The biggest trouble that ransomware actors will seek to address going forward is how they might maintain and cultivate strong reputations, which will heavily impact how they operate and promote themselves in the long-term.
Read our 2024 Ransomware? What Ransomware? Report to gain more insights into the current ransomware threat landscape from an open source intelligence perspective.

